MrRobot CyberDefenders-Writeup
Tools:
- Volatility2
- Volatility3
Description:
An employee reported that his machine started to act strangely after receiving a suspicious email for a security update. The incident response team captured a couple of memory dumps from the suspected machines for further inspection. Analyze the dumps and help the SOC analysts team figure out what happened!
Q1) Machine:Target1 What email address tricked the front desk employee into installing a security update?
After unzipping the file, I began the investigation by running imageinfo to gather the OS information that will be needed for the profile parameter. Which was Win7SP1x86_23418.
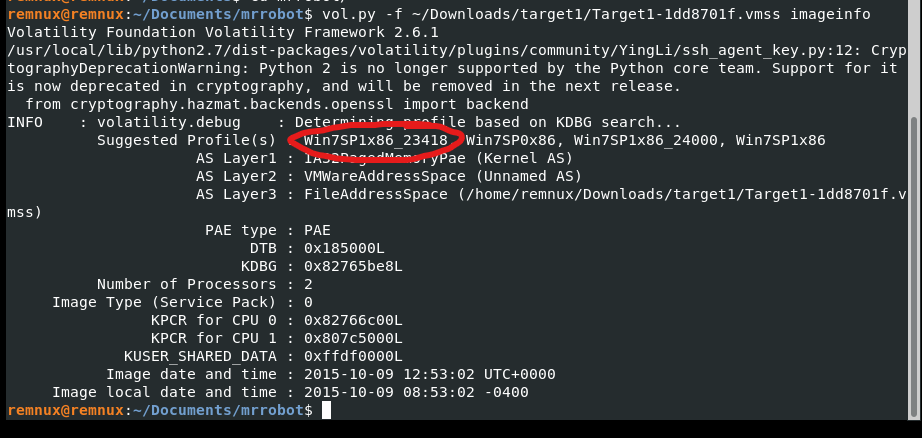
I then ran a series of processes-related plugins in an effort to provide more context and find any suspicious activity at the time the memory dump was taken. The output of pslist displays a number of suspicious processes that we should look into considering the situation described in the description. (outlook.exe,mstsc.exe,teamviewer.exe,) I also noticed a couple of things that were …interesting, the absence of the parent process of the teamviewer process and iexplorer in the pslist and pstree results, and the child process of iexplorer which was cmd.exe a red flag. Nonetheless, we shall proceed with the file scan plugin to see if there is a file that we can find that might be connected to the phishing email given the presence of the Outlook email client.
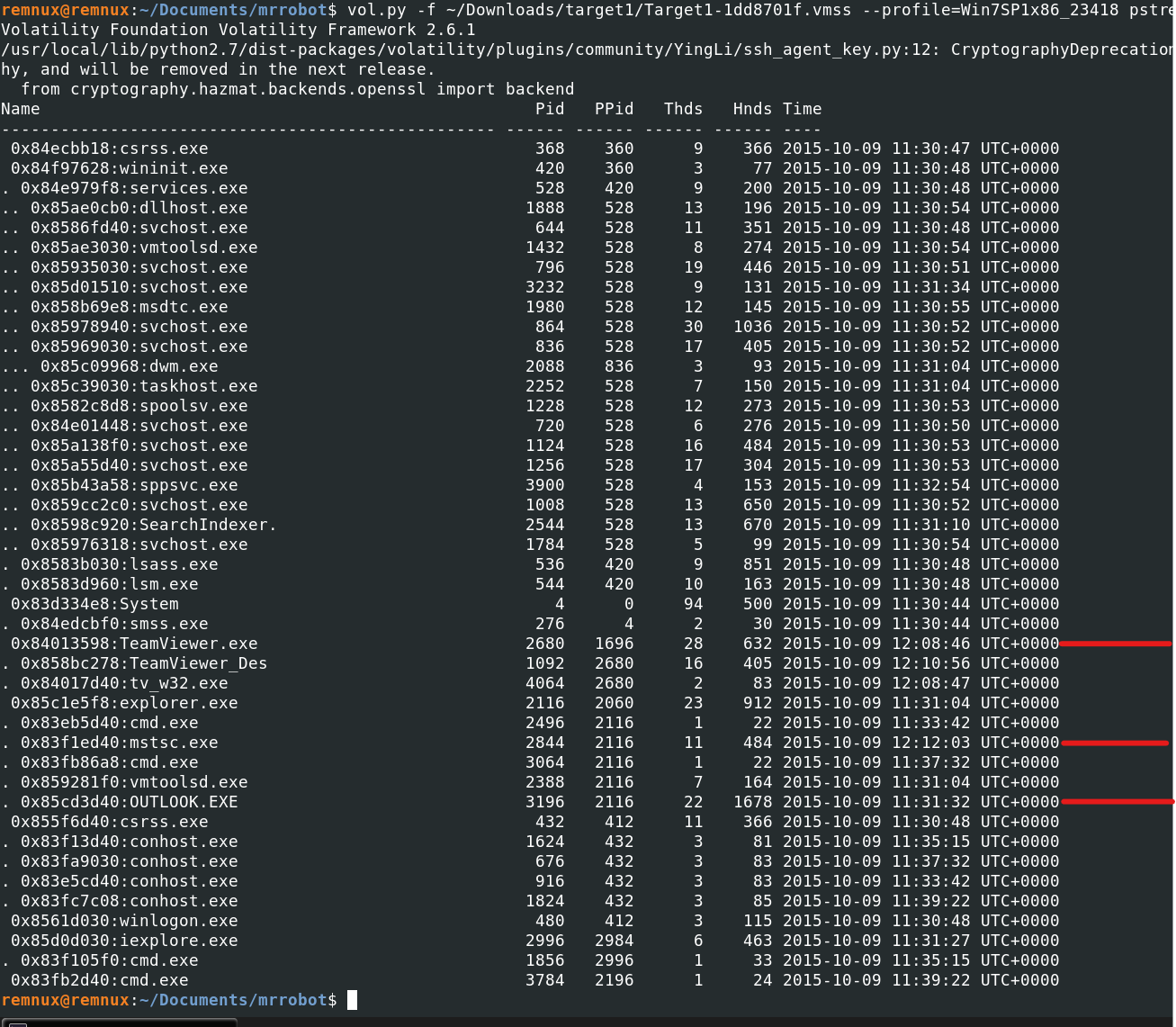
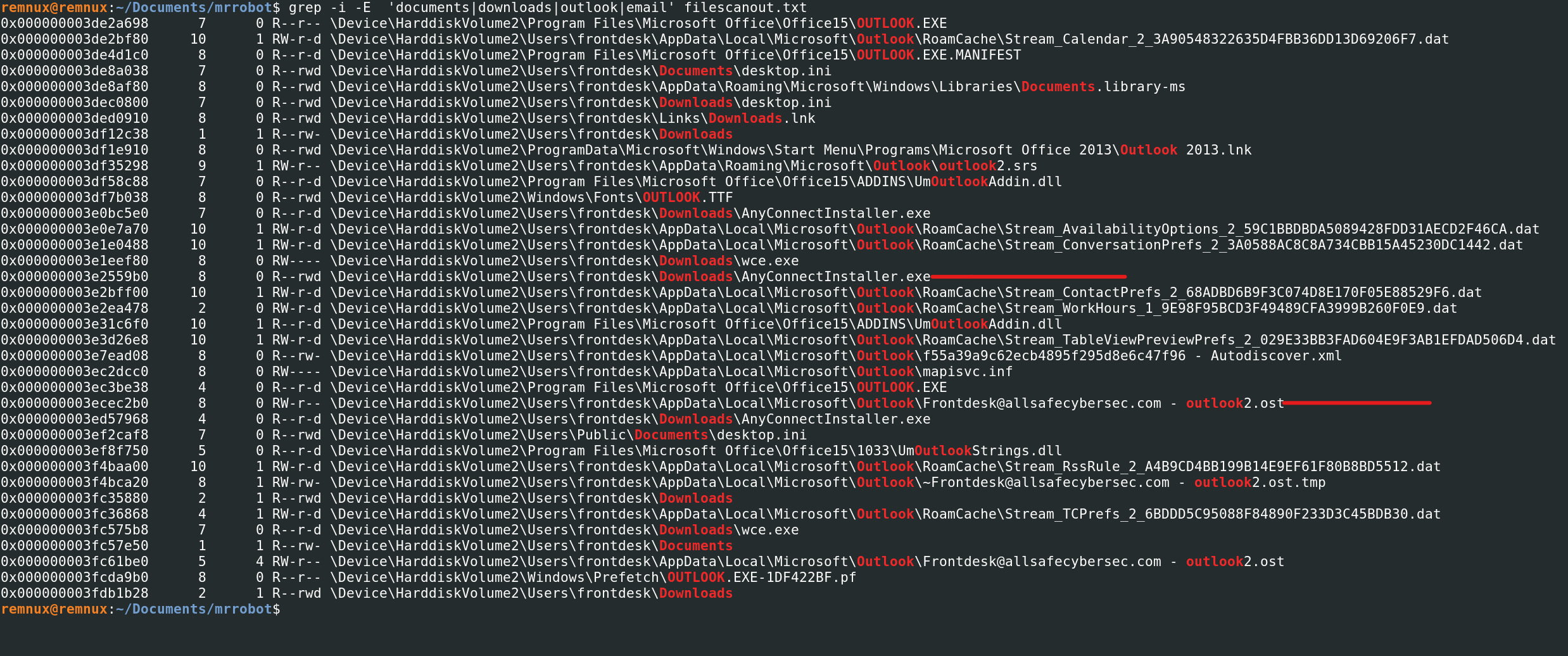
After utilizing the filescan plugin i greped for (Downloads, Documents, Temp, email, outlook,). a ost file was found (there was also an Anyconnect.exe in the downloads folder, something to keep in mind).
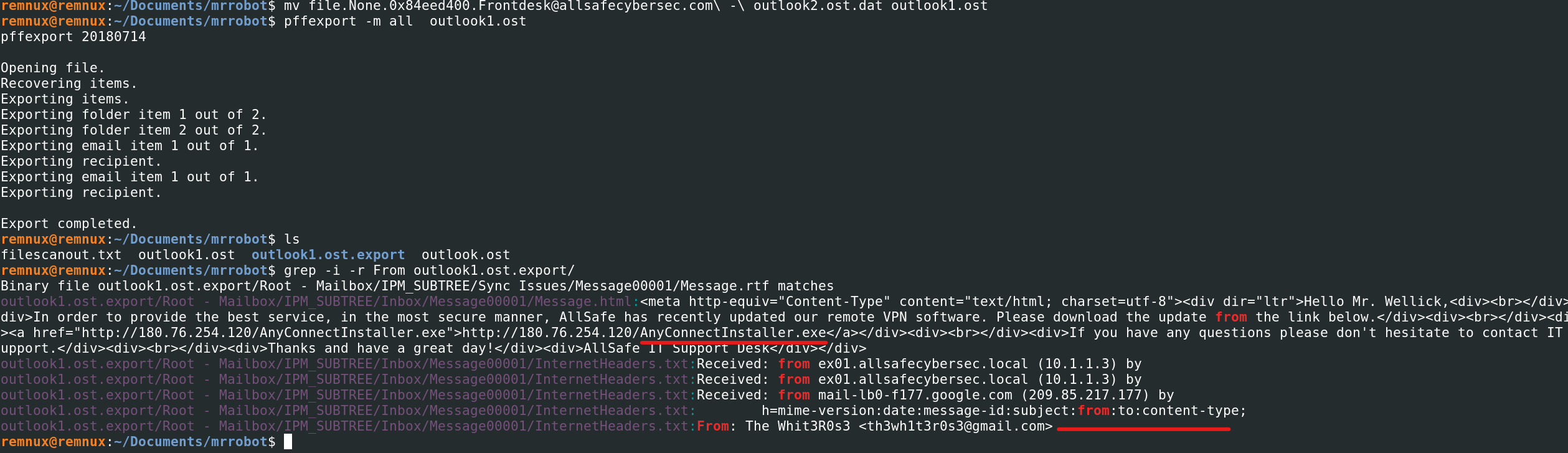
In order to be able to view the contents of the said file you will need to rename it to its original extension in this case .ost and pull the data from the ost file using the pffexport tool. I then used the command grep -r -i From outlook1.ost.export/ and found the phishing email that was sent to the victim along with the attachment which happened to be the executable we found in the downloads folder earlier.
Q2) Machine:Target1 What is the filename that was delivered in the email?
This was found in the results of the command that was used in q1.
Q3) Machine:Target1 What is the name of the rat’s family used by the attacker?
Now that we have identified the file that was downloaded the next logical step is to dump it for further analysis by running the command vol.py -f ~/Downloads/target1/Target1-1dd8701f.vmss --profile=Win7SP1x86_23418 dumpfiles -D . -n -u -Q (offset), i subsequently got the hash and submitted it to virus total to gather more details about it .
This was found by looking at the various names the AV Vendors gave it and referring to the format requested in the question.
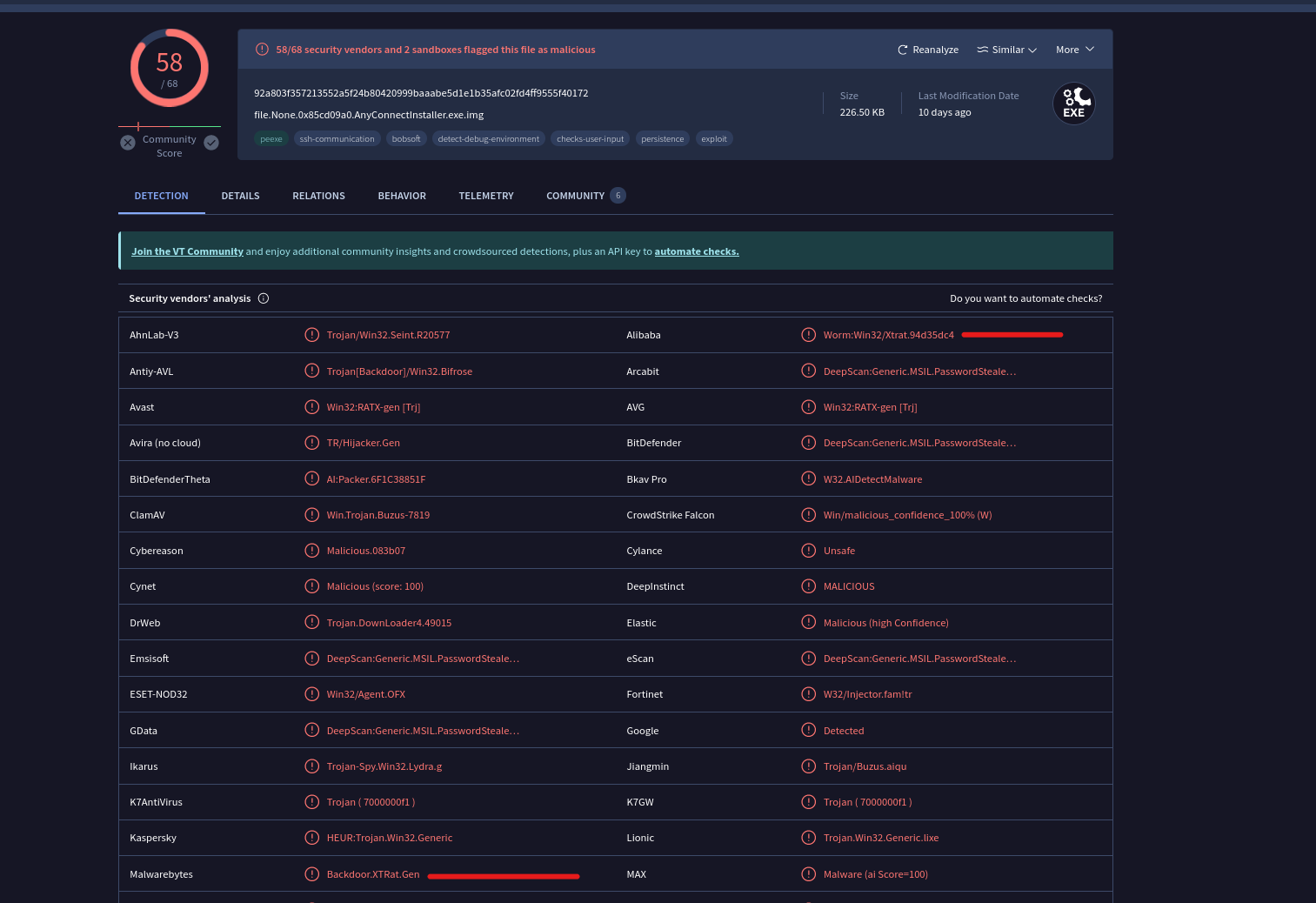
Q4) Machine:Target1 The malware appears to be leveraging process injection. What is the PID of the process that is injected?
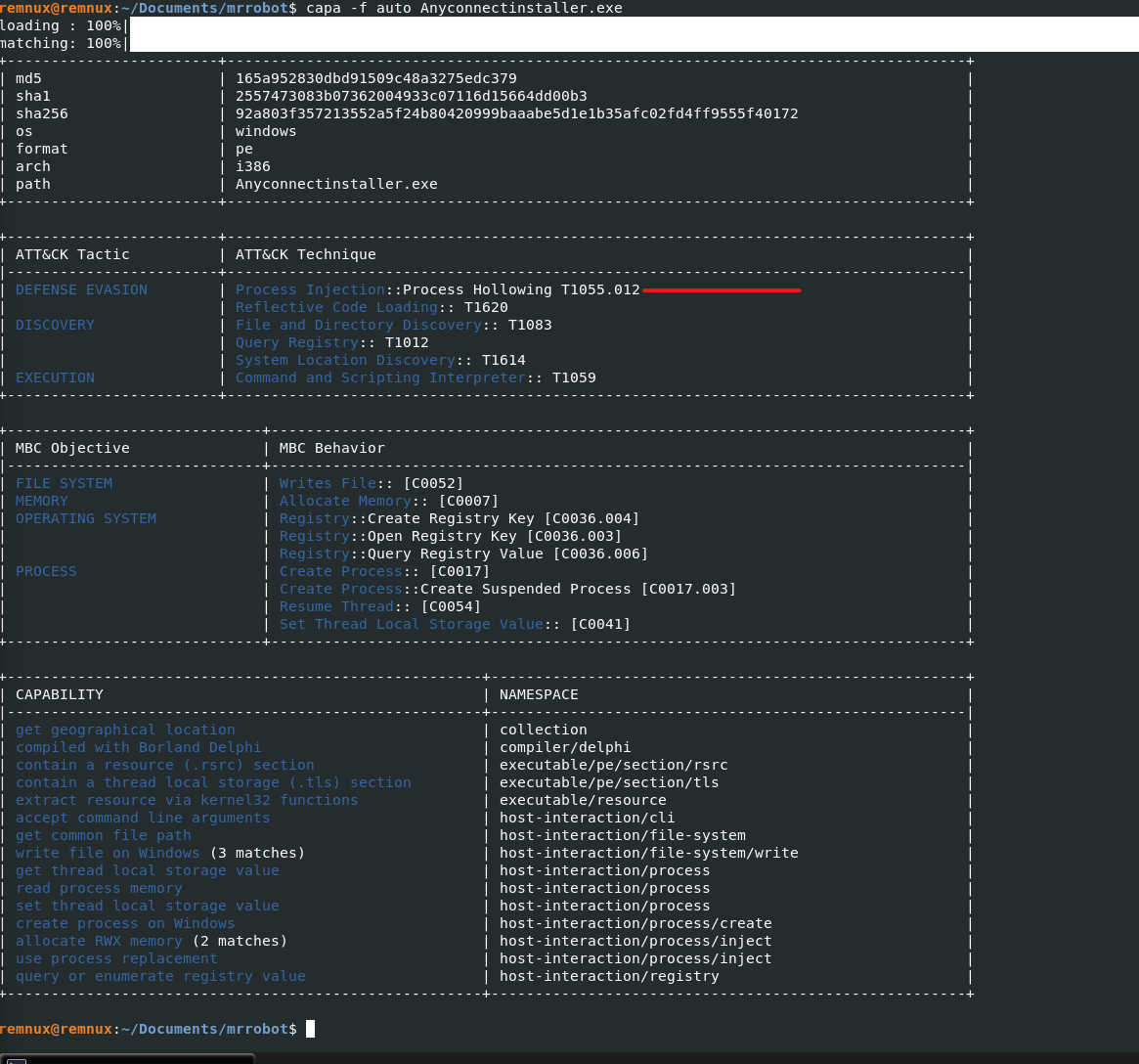
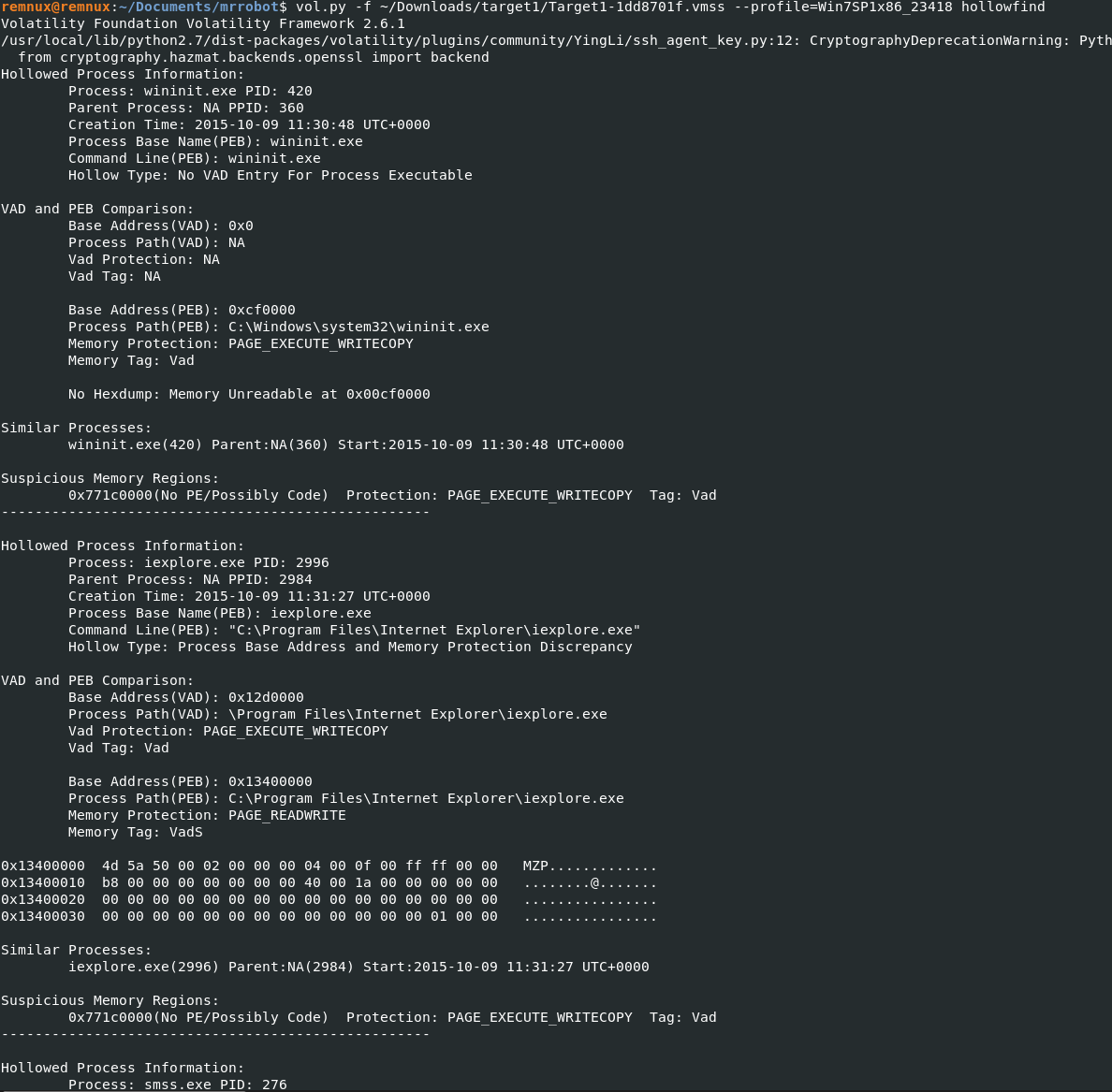
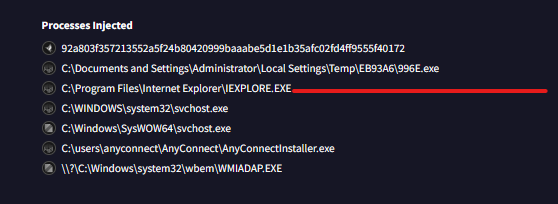
I used the capa tool to run a quick static analysis of the executable file and found that it was using the Process Hollowing technique to achieve process injection. Luckily there is a plugin for that “hollowfind” and were met with various results. We can look at the virus total report for confirmation. We find that iexlporer 2996 is being injected.
Q5) Machine:Target1 What is the unique value the malware is using to maintain persistence after reboot?
This can be found in the virustotal report as well in Behavior Tab.
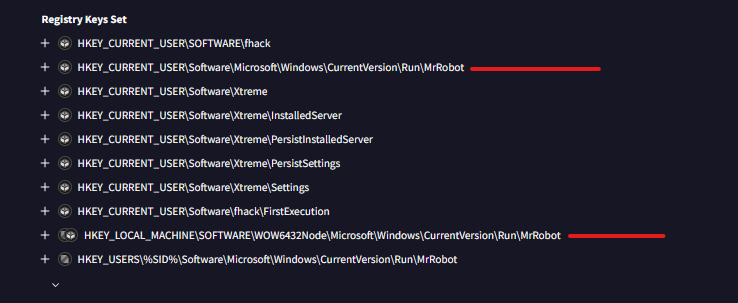
Q6) Machine:Target1 Malware often uses a unique value or name to ensure that only one copy runs on the system. What is the unique name the malware is using?
This is referred to as mutex and manages the accessibility of a shared resource by multiple threads typically a section of code, in this case, it ensures that only one instance of the malware is running to prevent a larger footprint and possibly go down the execution chain instead of repeating the same steps.
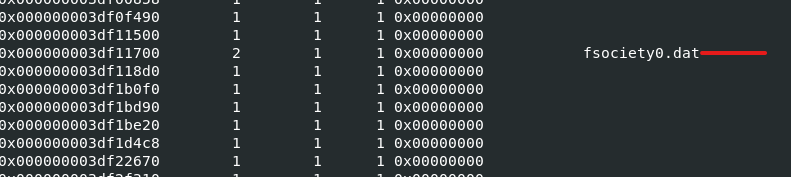
I employed the use of the mutantscan plugin and referred to the format in the question and found fsociety0.dat in the result.
 Q7) Machine:Target1 It appears that a notorious hacker compromised this box before our current attackers. Name the movie he or she is from.
Q7) Machine:Target1 It appears that a notorious hacker compromised this box before our current attackers. Name the movie he or she is from.
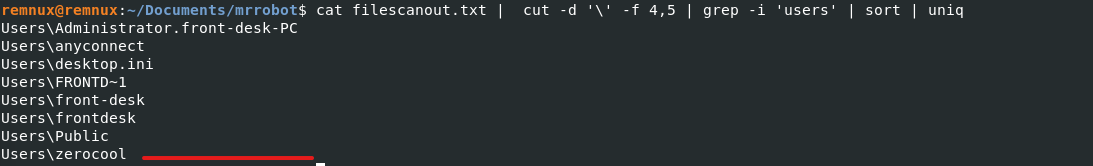
I used the filescan txt file i created and searched for any entries of the following \Users\ with cat filescanout.txt | cut -d '\' -f 4,5 | grep -i 'users' | sort | uniq the only one that was quite distcint was ‘zerocool’ a quick google search confirmed that this was indeed the answer.
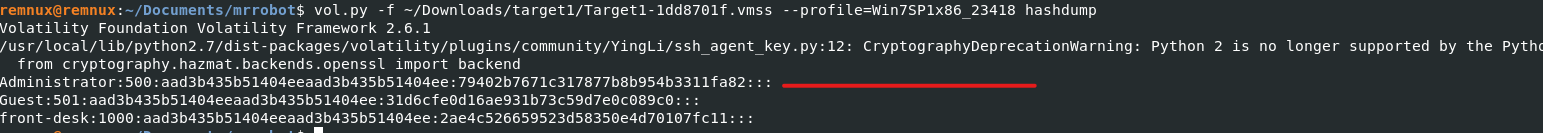
Q8) Machine:Target1 What is the NTLM password hash for the administrator account?
This can be found by running the hashdump plugin.
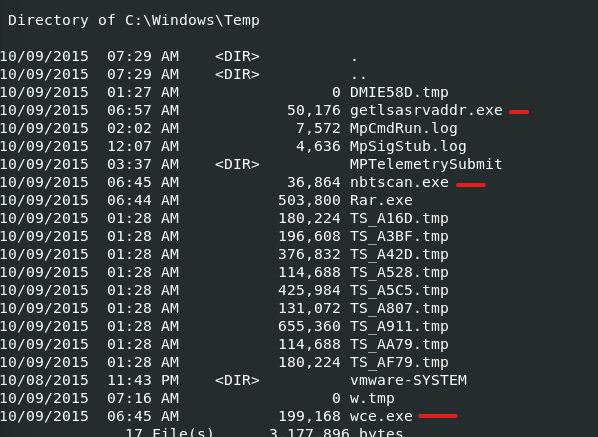
Q9) Machine:Target1 The attackers appear to have moved over some tools to the compromised front desk host. How many tools did the attacker move?
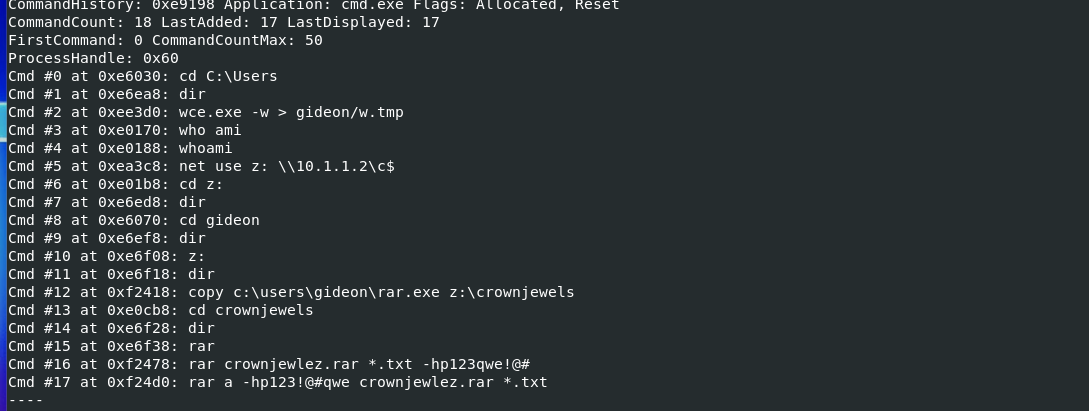
Using the consoles plugin we can see the command history. Looking through the results we some interaction within the temp dir.
4 executable files are found:
- getlsasrvaddr.exe - used to obtain the needed addresses for wce
- Rar.exe - file compression tool
- wce.exe - windows crendential editor obtain NTLM hashes from memory
- nbtscan.exe - netbios enumeration tool
3 Tools were found wce, rar, and nbt.
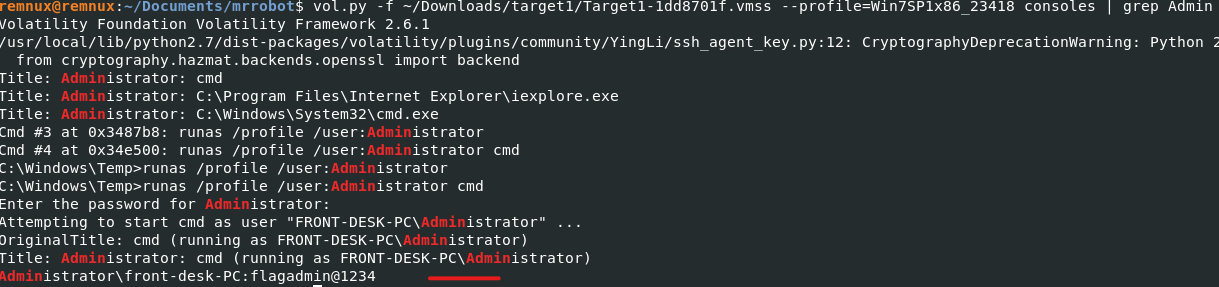
Q10) Machine:Target1 What is the password for the front desk local administrator account?
I greped using the consoles plugin.
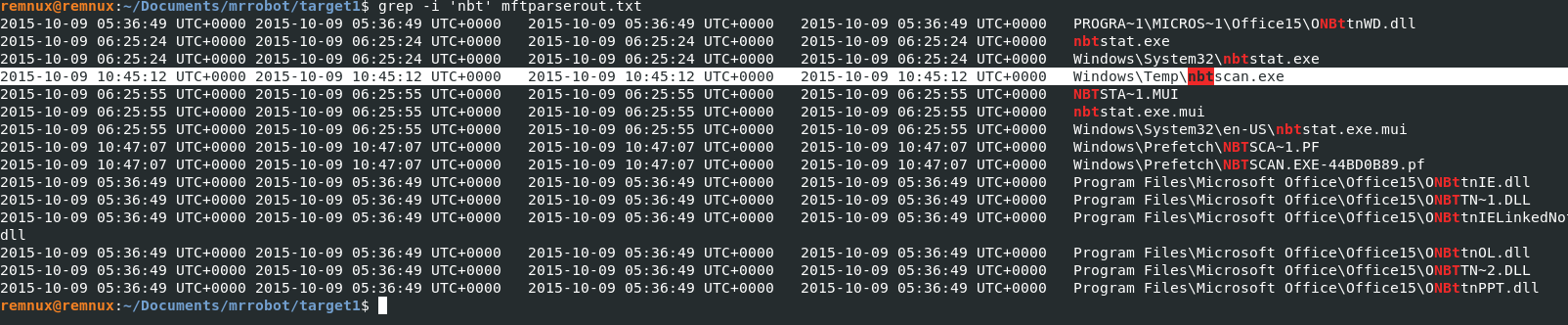
 Q11) Machine:Target1 What is the std create data timestamp for the nbtscan.exe tool?
Q11) Machine:Target1 What is the std create data timestamp for the nbtscan.exe tool?
To answer this question I created a .txt file for the mftparser (Displays creation, modification, and access timestamps) output and greped for nbt which displayed the timestamp for the creation of the file.grep -i 'nbt' mftparserout.txt
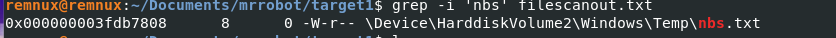
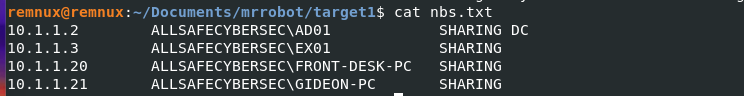
Q12) Machine:Target1 The attackers appear to have stored the output from the nbtscan.exe tool in a text file on a disk called nbs.txt. What is the IP address of the first machine in that file?
Using the filescan txt file I ran grep -i 'nbs' filescanout.txt, dumped the file, renamed it, and read its contents.
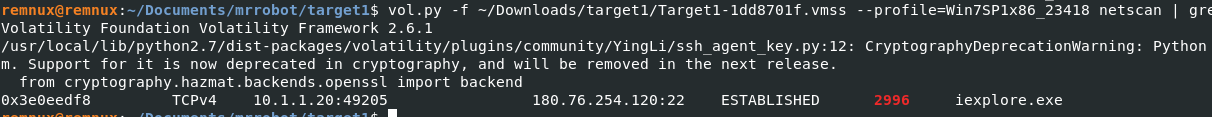
Q13) Machine:Target1 What is the full IP address and the port was the attacker’s malware using?
We can find this the answer by running the netscan plugin. Earlier we had discovered that the malicious process that was running was iexplorer which was injected PID 2996. vol.py -f ~/Downloads/target1/Target1-1dd8701f.vmss --profile=Win7SP1x86_23418 netscan | grep 2996
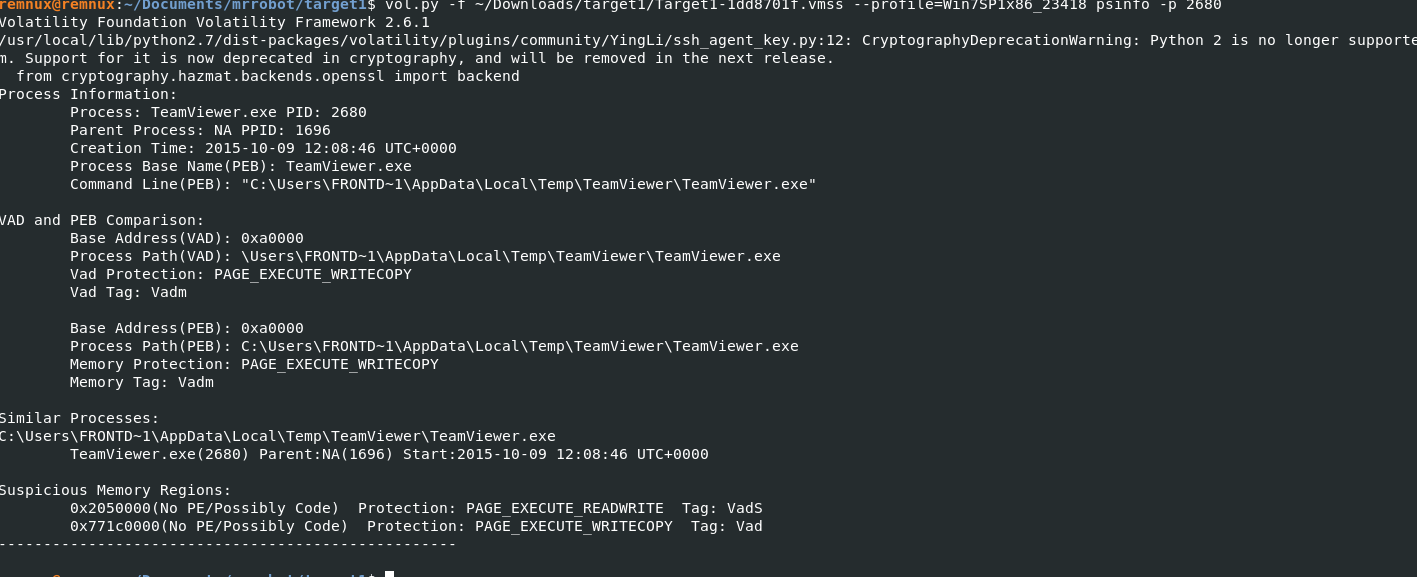
Q14) Machine:Target1 It appears the attacker also installed legit remote administration software. What is the name of the running process?
Referring back to q1, I mentioned the various remote administration tools that were present in the output of pslist which initially caught my attention. One of these is Teamviewer.exe PID 2680, to confirm my suspicion I ran the psinfo against that pid and it found the presence of PAGE_EXECUTE_READWRITE, coupled with the fact that there were only two remote admin tools made it pretty obvious that the answer was Teamviewer.exe
Q15) Machine:Target1 It appears the attackers also used a built-in remote access method. What IP address did they connect to?
The questions states “built-in remote access method”, the only remote built-in access method that exists within the memory dump is mstsc.exe or RDP. I ran vol.py -f ~/Downloads/target1/Target1-1dd8701f.vmss --profile=Win7SP1x86_23418 netscan | grep mstsc.exe and found the dst ip:port.
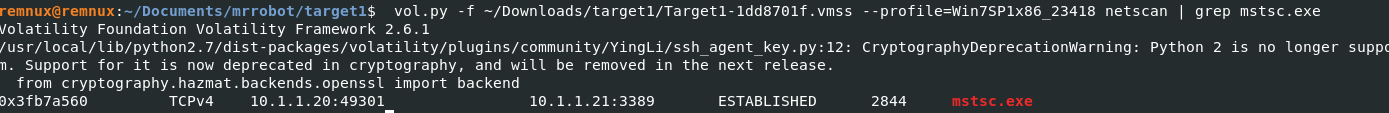
Q16) Machine:Target2 It appears the attacker moved latterly from the front desk machine to the security admins (Gideon) machine and dumped the passwords. What is Gideon’s password?
Moving on to the target2 memory dump, I used the vol.py -f ~/Downloads/target2/target2-6186fe9f.vmss --profile=Win7SP1x86_23418 consoles to see if any commands were used to dump the passwords.
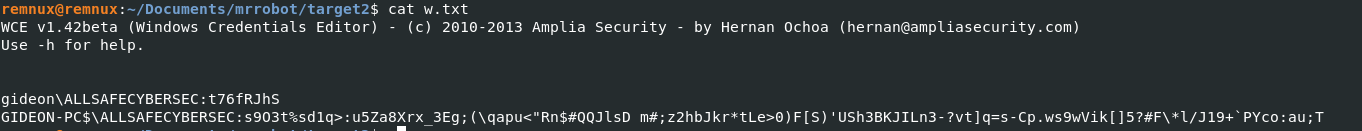
Now i recall the function of the wce.exe tool was to obtain the creds/NTLM Hashes of a user, within the consoles plugin results we see the hacker outputting the information to a text file called ‘w.txt’. That prompted me to run the filescan plugin grep for w.txt, dump the file, rename it, and read the contents of it which stored the dumped password for “Gideon”
Q17) Machine:Target2 Once the attacker gained access to “Gideon,” they pivoted to the AllSafeCyberSec domain controller to steal files. It appears they were successful. What password did they use?
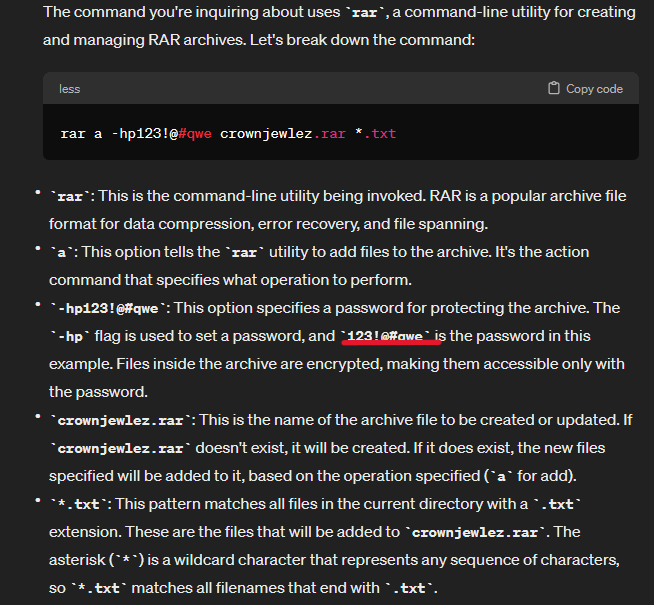
I initially thought the answer was “-hp123!@#qwe” but i was met with a “invalid answer. So i did some research.
Chatgpt is a great resource to decipher the function of the commands that were run; however, be sure to double-check the answers. That being said it seems like the -hp is part is an argument that sets a password ie the characters following “-hp” for the archive “crownjewelez.rar” that adds all the text files that reside in the cwd.
Q18) Machine:Target2 What was the name of the RAR file created by the attackers?
The answer was the rar file named “crownjewelez.rar”
Q19) Machine:Target2 How many files did the attacker add to the RAR archive?
At first, I ran both the mftparser plugin and filescan and filtered for the rar file. Obviously, nothing was returned considering the fact that this was done on a fileshare on the domain controller. So I had to look for alternative ways to obtain the desired information. Namely, using the memorydump plugin on the conhost.exe 3048 PID process and filtering for the rar file there. using the command strings -a -el 3048.dmp | grep 'txt'
Scrolling down a bit I noticed the commands that were ran and the text files that were added to the archive. 3
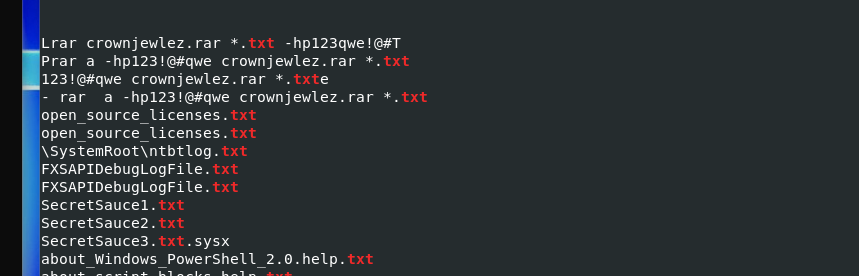
Q20) Machine:Target2 The attacker appears to have created a scheduled task on Gideon’s machine. What is the name of the file associated with the scheduled task?
I utilized the filescan txt file i created and searched for tasks using cat filescanout.txt | grep -i tasks Noticed two entries that were out of place “at1” and “at1.job”. a quick Google search says they’re often associated with malware. Guess that means we’re dumping it haha. vol.py -f ~/Downloads/target2/target2-6186fe9f.vmss --profile=Win7SP1x86_23418 dumpfiles -D . -n -Q 0x000000003fd05bd8, mv file.None.0x84135948.At1.job.dat at1.job, strings -a -el at1.job
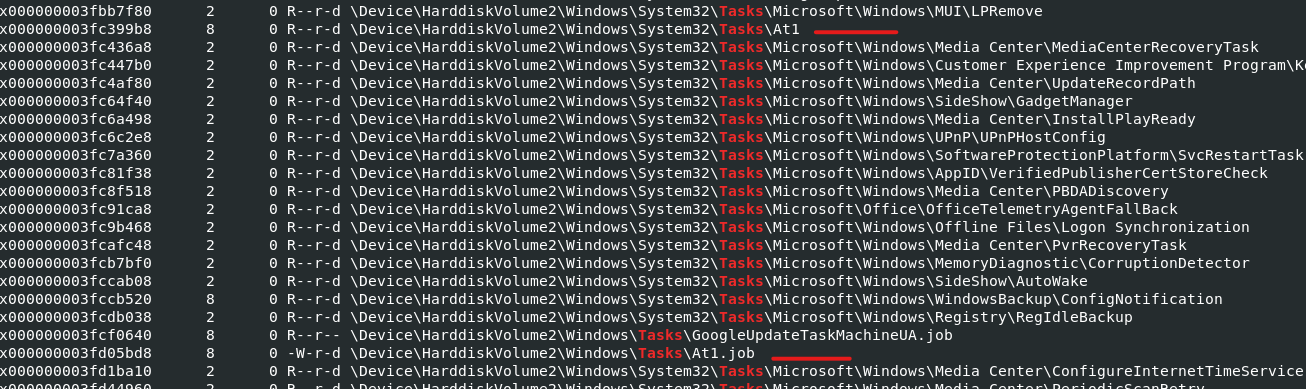
The file is 1.bat
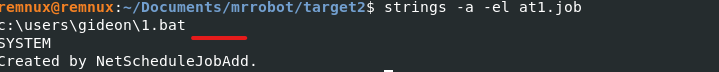
Q21) Machine:POS What is the malware CNC’s server?
Based on the question I executed the netscan plugin and took a good look at the outbound connections. I took notice of iexplorer as that has been the common denominator among target1 and target2 machines at first I dumped the process using procdump and scanned it with capa but it seems like it was just a regular exe file, for confirmation I ran malfind on that process for more details. Results indicate it was malicious. More than likely leveraging process injection.
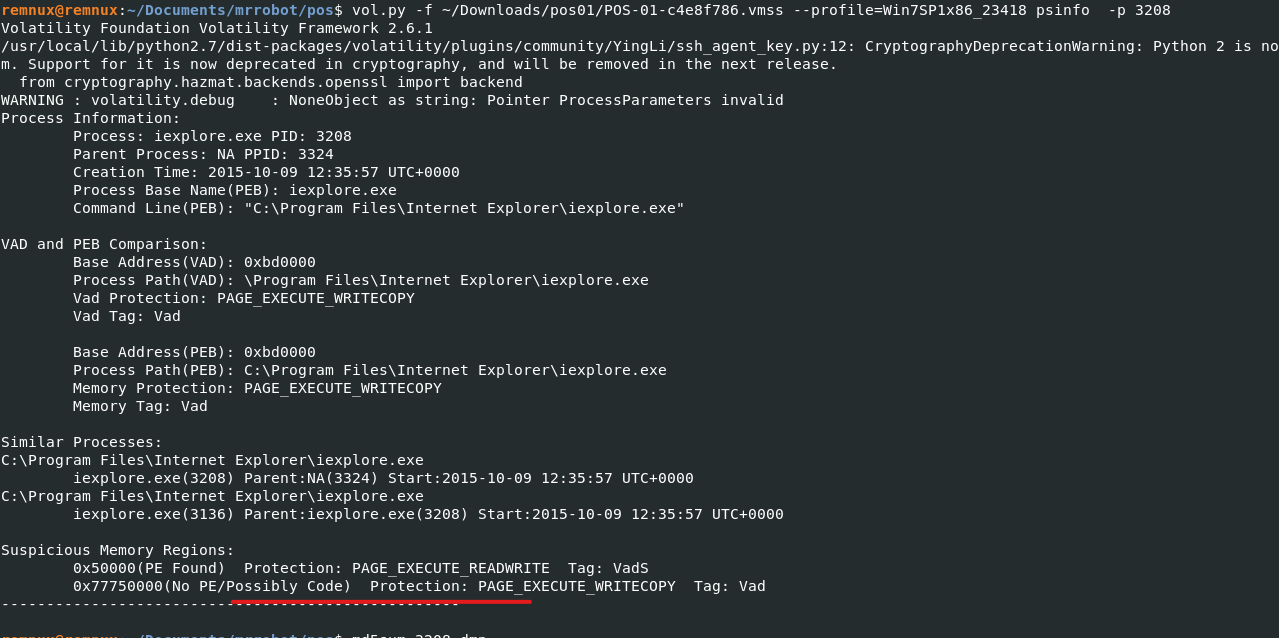
I then ran iehistory given the use of internet explorer and parsed through the displayed information which revealed an executable file that was downloaded from the ip we saw iexplorer connecting to.
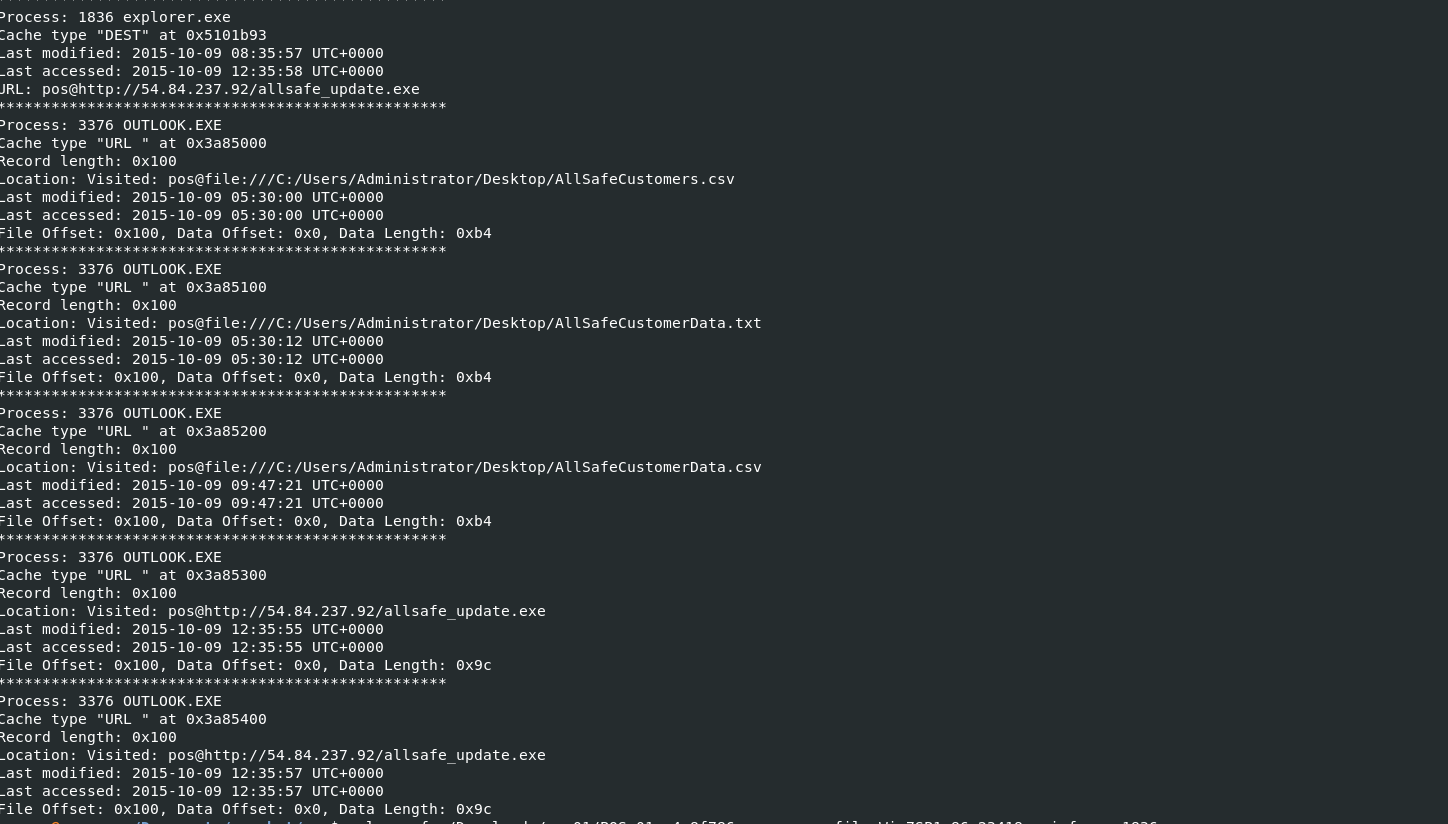
I used the filescan plugin and searched for allsafe_update.exe, dumped it, ran capa which confirmed it was a malicious file.
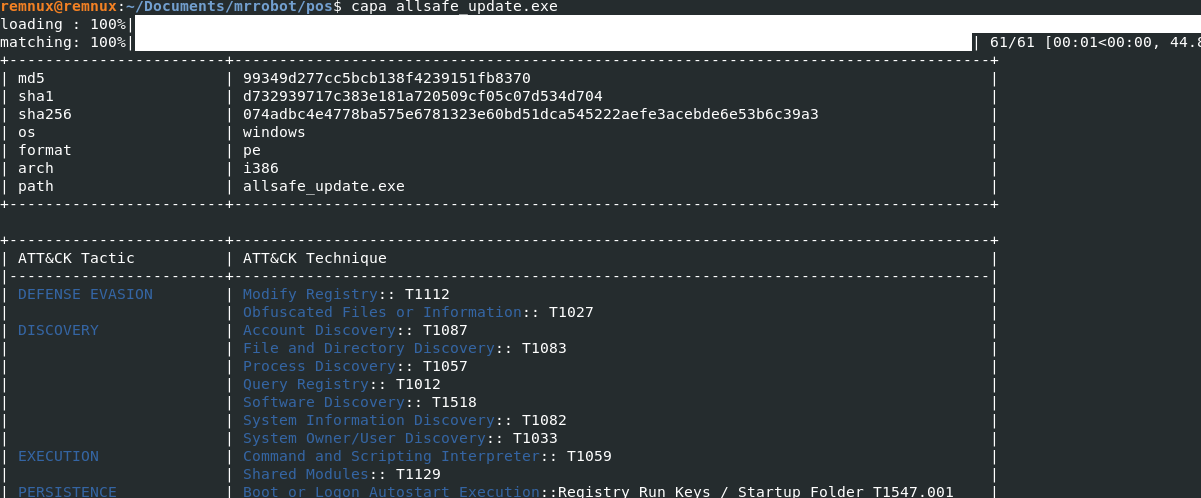
Just for good measure I used the memdump plugin on the iexplorer process and greped for allsafe_update.exe. The outcome was satisfactory. I guess you can say it was an allsafe bet from the beginning? haha
Q22) Machine:POS What is the common name of the malware used to infect the POS system?
Took the hash from capa results and submitted it to virustotal.
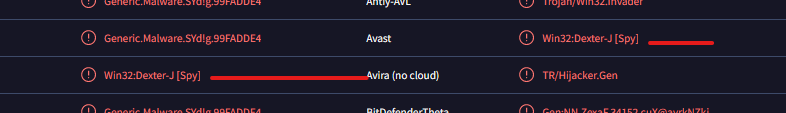
Q23) Machine:POS In the POS malware whitelist. What application was specific to Allsafecybersec?
This took me a while due to not understanding the question but eventually, I figured out they were referring to the malware itself and its contents, i ran peframe and found allsafe_protector.exe within the allsafe_update.exe file.
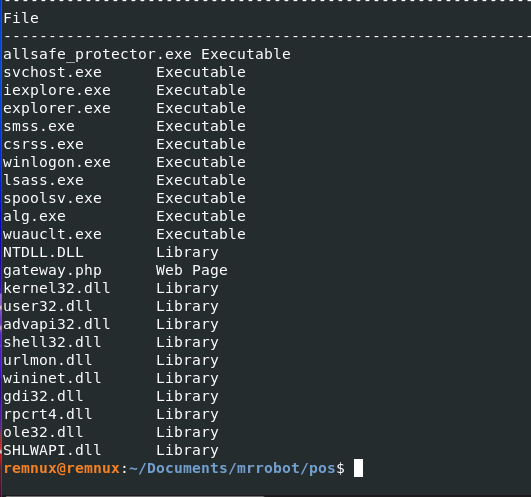
Q24) Machine:POS What is the name of the file the malware was initially launched from?
The malware was initially launched from allsafe_update.exe found in q21.