FalconEye CyberDefenders-Writeup
Description:
As a SOC analyst, you aim to investigate a security breach in an Active Directory network using Splunk SIEM (Security information and event management) solution to uncover the attacker’s steps and techniques while creating a timeline of their activities. The investigation begins with network enumeration to identify potential vulnerabilities. Using a specialized privilege escalation tool, the attacker exploited an unquoted service path vulnerability in a specific process.
Once the attacker had elevated access, the attacker launched a DCsync attack to extract sensitive data from the Active Directory domain controller, compromising user accounts. The attacker employed evasion techniques to avoid detection and utilized pass-the-hash (pth) attack to gain unauthorized access to user accounts. Pivoting through the network, the attacker explored different systems and established persistence.
Throughout the investigation, tracking the attacker’s activities and creating a comprehensive timeline is crucial. This will provide valuable insights into the attack and aid in identifying potential gaps in the network’s security.escription:
As a SOC analyst, you aim to investigate a security breach in an Active Directory network using Splunk SIEM (Security information and event management) solution to uncover the attacker’s steps and techniques while creating a timeline of their activities. The investigation begins with network enumeration to identify potential vulnerabilities. Using a specialized privilege escalation tool, the attacker exploited an unquoted service path vulnerability in a specific process.
Once the attacker had elevated access, the attacker launched a DCsync attack to extract sensitive data from the Active Directory domain controller, compromising user accounts. The attacker employed evasion techniques to avoid detection and utilized pass-the-hash (pth) attack to gain unauthorized access to user accounts. Pivoting through the network, the attacker explored different systems and established persistence.
Throughout the investigation, tracking the attacker’s activities and creating a comprehensive timeline is crucial. This will provide valuable insights into the attack and aid in identifying potential gaps in the network’s security.
Q1) Mchine:Target1 What is the name of the compromised account?
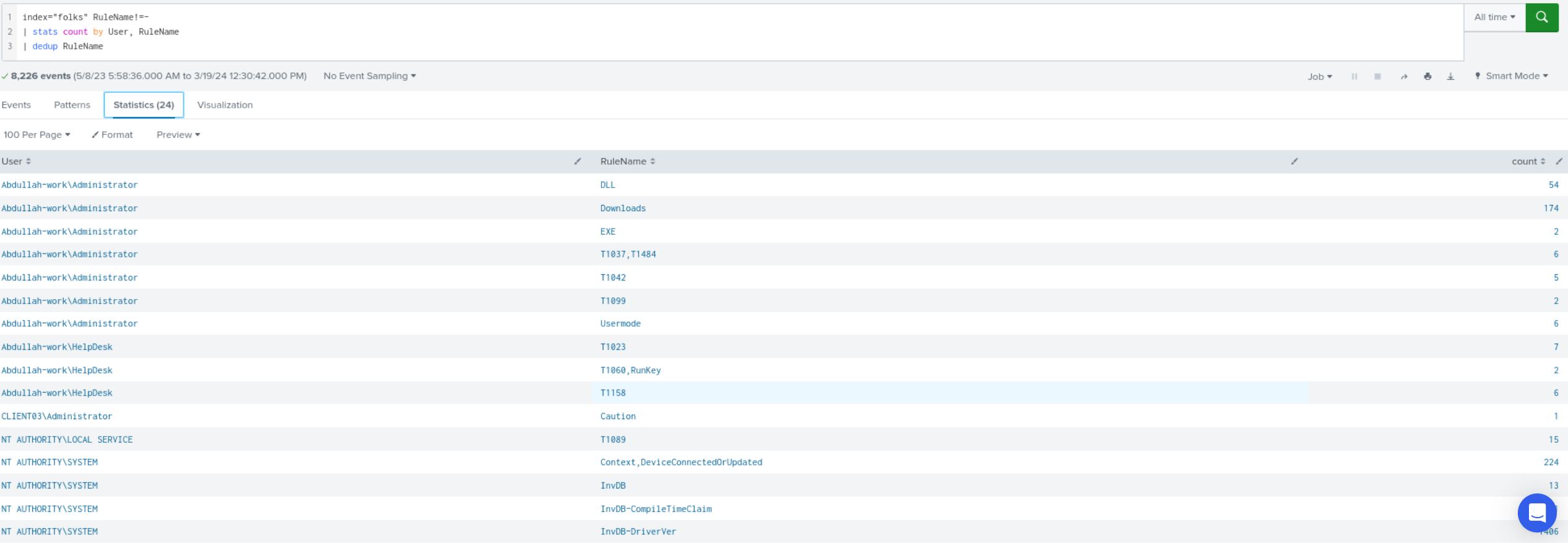
Before I began, I looked through the available fields that I could use to help me find the answer, I figured the User, Rulename, fields could assist me in identifying the users that triggered a Rule. From there, I’d use a more detailed search query to pinpoint what user was compromised first.
I utilized the following search query to narrow down the potential users that might been compromised. index="folks" RuleName!=- | stats ccount by User, RuleName | dedup RulenName. There were two system accounts, one local administrator account, and two user accounts (Abdullah-work\Administrator,Abdullah-work\HelpDesk) The Administrator triggered the “Downloads” rule over 170 so perhaps one of the tools they used to enumerate the environment was one of them. I’m guessing they somehow performed some privilege escalation to move from the helpdesk account to the administrator account; However, we should not assume but verify.
index="folks" RuleName!=- User IN ("Abdullah-work\\Administrator", "Abdullah-work\\HelpDesk") | table _time Computer User Description EventID ProcessId Image cmdline ParentProcessId ParentCommandLine registry_path RuleName
There was a lot of noise in the process_name so I added dedup to exclude any duplicates and found something pretty suspicious originating from the helpdesk account, an executable named “fun.exe” and the use of PowerShell, which is not suspicious in of itself but it does not hurt to ensure that it’s not being used maliciously.
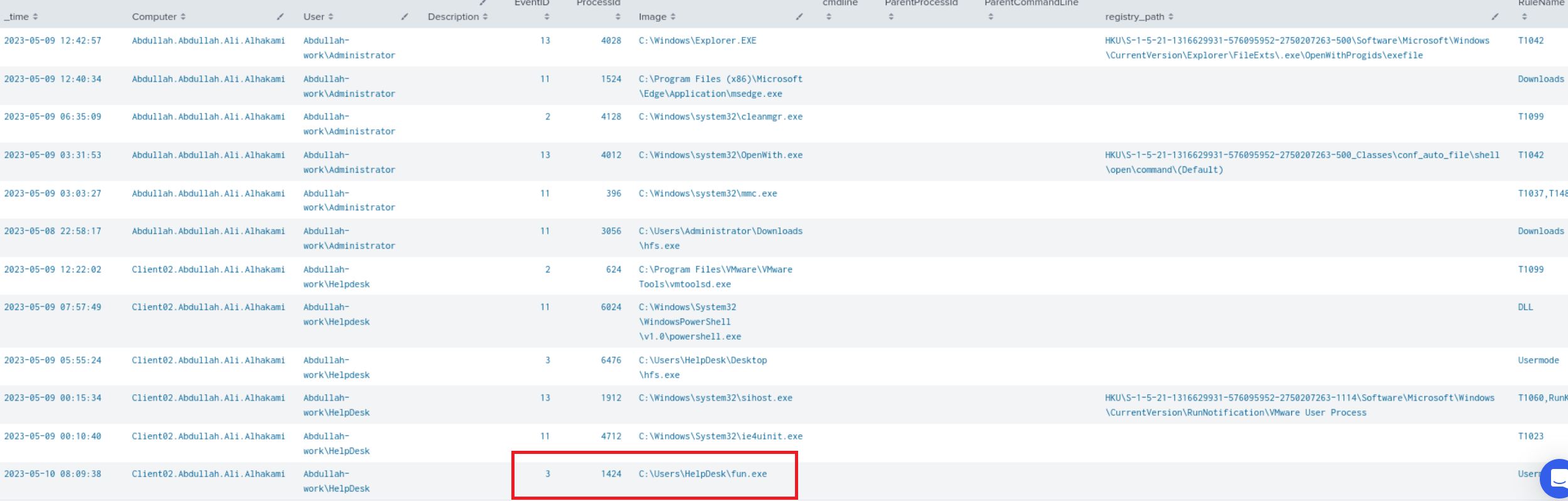
I then filtered just for the helpdesk user and spotted another suspicious executable “Better-to-trust.exe” Got the SHA256 hash for both “Better-to-trust.exe” and “fun.exe” and submitted it to virustotal, pretty obvious this was the account that was compromised given the presence of these (mimikatz, and rubeus) offensive tools.
I then decided to run the query without dedup as the results for the past query did not yield any cmdline arguments so I thought I was over-filtering.
index="folks" User="Abdullah-work\\HelpDesk" | table _time Description EventID ProcessId Image cmdline ParentProcessId ParentCommandLine registry_path RuleName
Upon scrolling through the first few results I did not find anything interesting; However, after sorting the time to descending i scrolled down a bit and found the command line arguements for the “fun.exe” and Better-to-help.exe along with a new one “Microsoft-Update.exe” the description field identified it as “Rubeus” quick google search states it’s a tool for “Kerberos interaction and abuses”
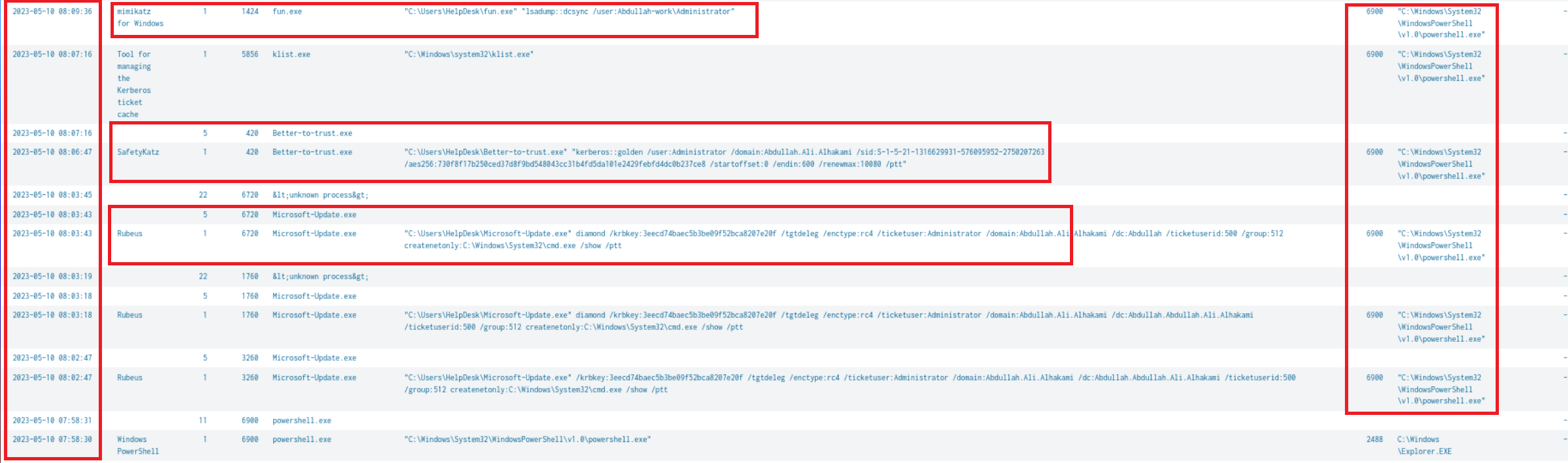
Now we have identified the parent process, PowerShell, a rough time frame from which these events occurred and the the different tools the threat actor used.
Q2) Machine:Target1 What is the name of the compromised machine?
This was one of the fields I included in my search query for Q1. “Client02”
Q3) Machine:Target1 What tool did the attacker use to enumerate the environment?
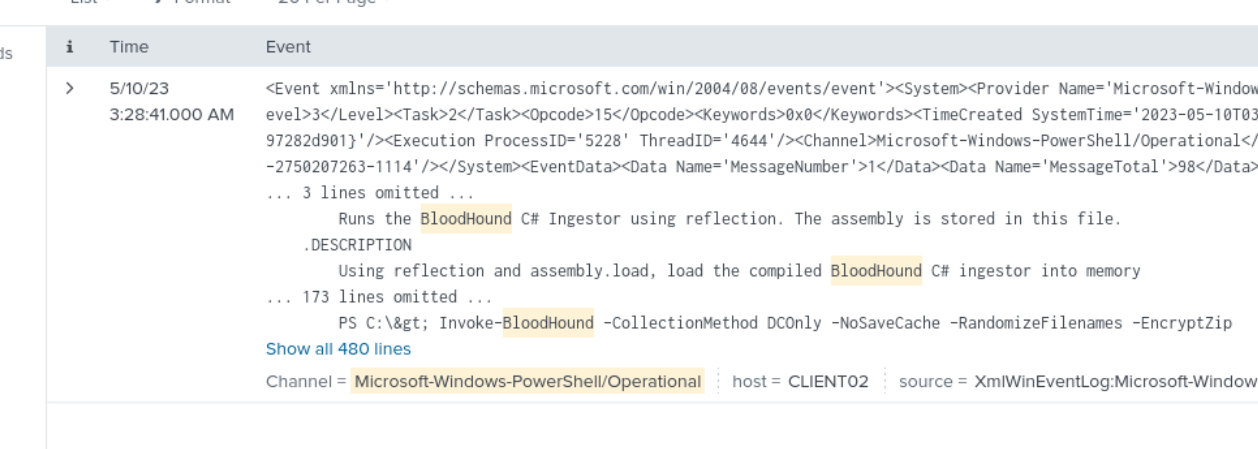
Considering PowerShell was used extensively in the attack, I filtered for event ID 4104 which is “execution of a PowerShell command”. I looked through various scriptblocktexts and discovered powersploit was here but that was not the answer. I searched up bloodhound as a shot in the dark as that a very popular tool to enumerate ad and got a hit.
index="folks" EventID=4104 bloodhound
Q4) Machine:Target1 The attacker used Unquoted Service Path to escalate privileges. What is the name of the vulnerable service?
While running the query in Q1 I noticed icacls.exe, at first i thought it was something malicious as I was not familiar with this native Windows program so I searched it up and read its purpose
Again, I was still a little suspicious given the fact that it’s used to edit permissions but I just made a note of it. That said, after running into this question I had to do some more external research about this vulnerability. Definitely suggest giving this a read https://juggernaut-sec.com/unquoted-service-paths/. The information was quite interesting specifically the potential use of icalcs.exe to exploit this vulnerability. So I queried for all instances of “icacls.exe” (took a long time since I had the wrong time filter set haha) but eventually I figured out that small mistake
index="folks" process_name="*icacls.exe*" | table _time User cmdline
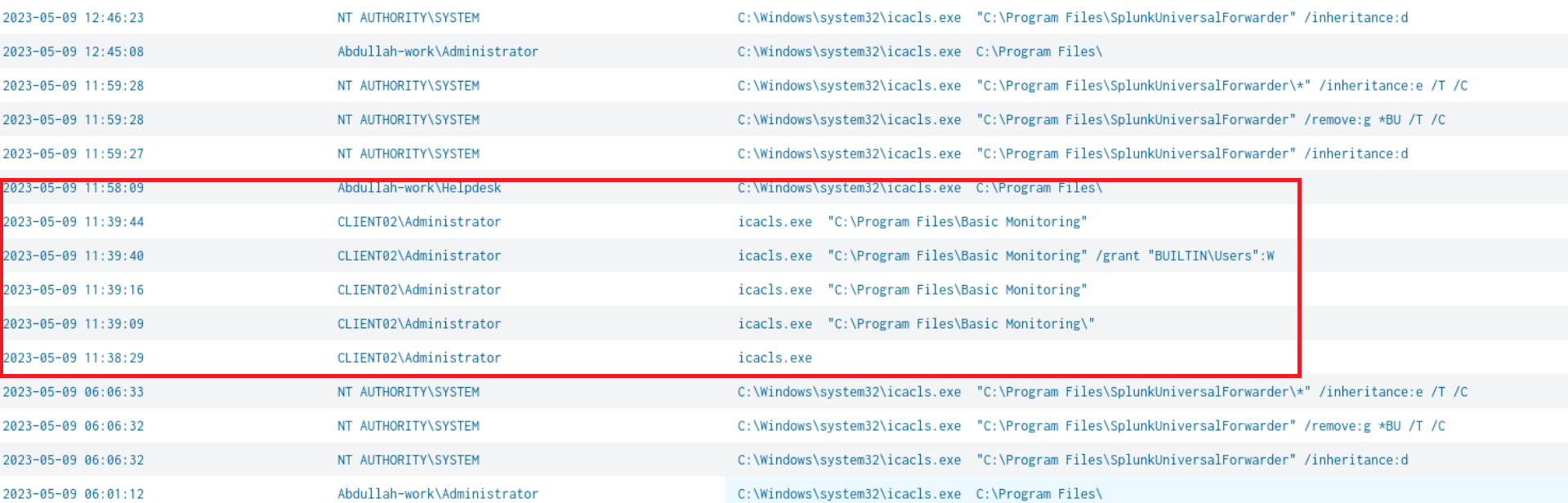
Most of cmdline arguments were splunk related besides, “icacls.exe “C:\Program Files\Basic Monitoring” /grant “BUILTIN\Users”:W”, This cmd is essentially giving write permissions to the “C:\Program Files\Basic Monitoring” directory, we can logically deduce that they might create a file in this directory. Utilizing the following query we found the vulnerable service.
index="folks" cmdline="*C:\\Program Files\\Basic Monitoring*" | table _time User cmdline
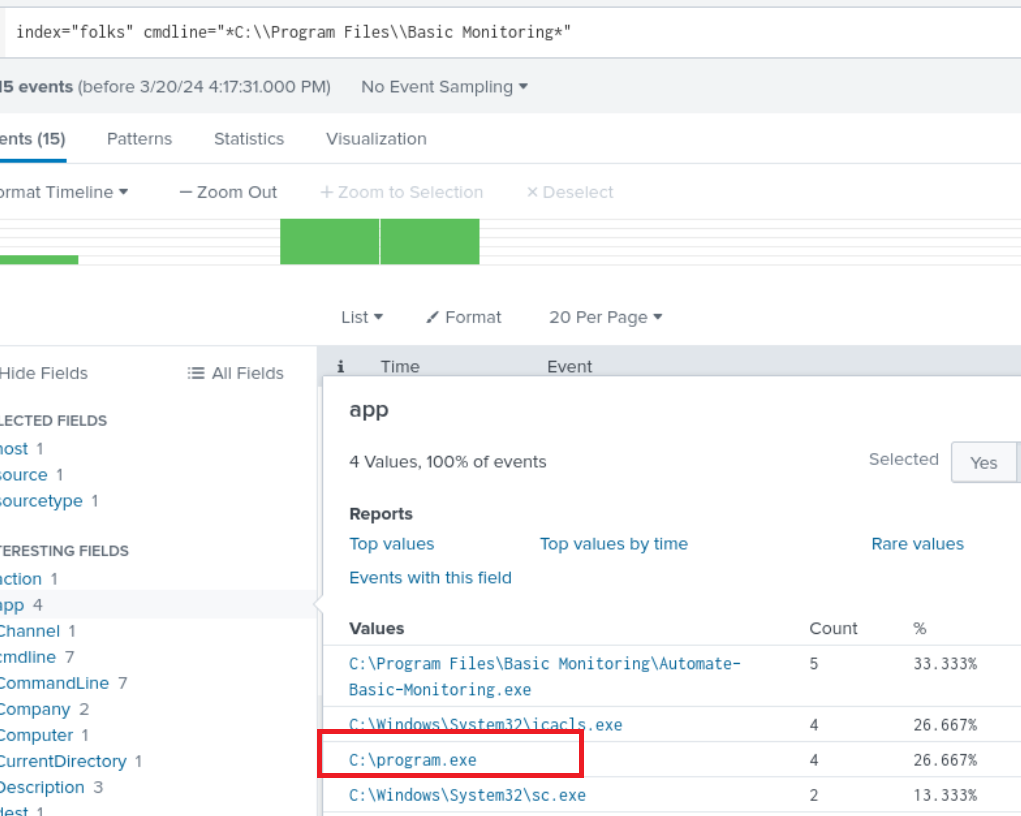
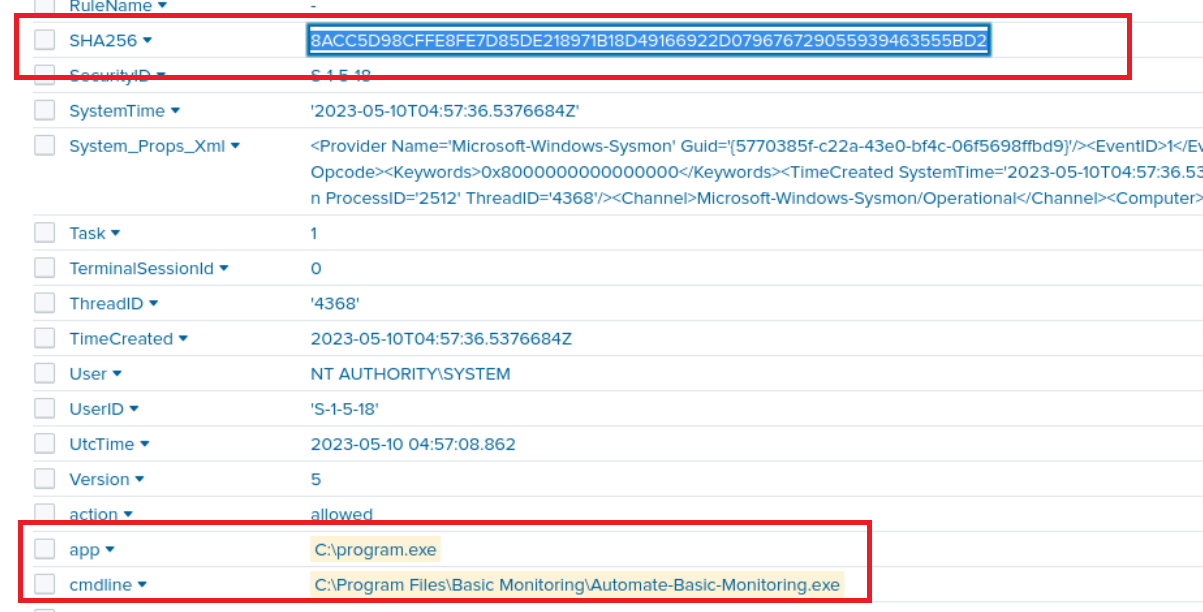
Q5) Machine:Target1 What is the SHA256 of the executable that escalates the attacker’s privileges?
Searching for the basic monitoring directory I looked in the apps field and it listed program.exe you just need the SHA256 hash of it.
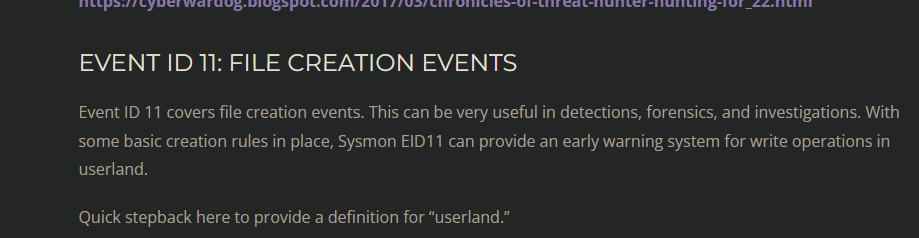
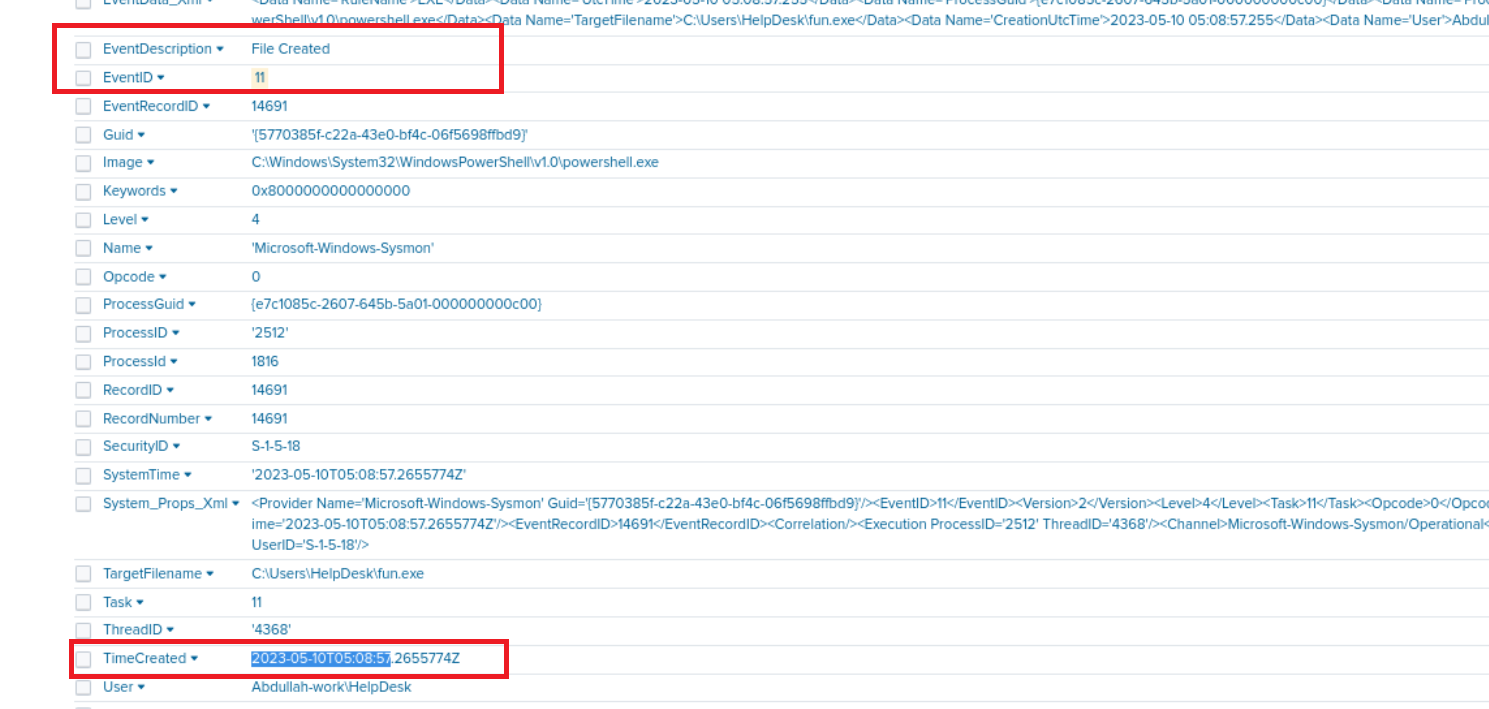
Q6) Machine:Target1 When did the attacker download fun.exe? (24H-UTC)
This was pretty straightforward, I simply used this search index="folk" search "*Fun.exe*" EventID=11
Q7) Machine:Target1 What is the command line used to launch the DCSync attack?
This was found in Q1 the user used, “fun.exe” to run the command

Q8) Machine:Target1 What is the original name of fun.exe?
I essentially ran the same search query I used in Q6 with the OriginalFileName field instead of EventID.
index="folk" search "*Fun.exe*" OriginalFileName="*"
Nonetheless, the Q1 query had the description column which classified it as “mimikatz for windows” and our submission of the hash already gave us the answer.

Q9) Machine:Target1 The attacker performed the Over-Pass-The-Hash technique. What is the AES256 hash of the account he attacked?
Taking into account the executables that we found in Q1 I refined the search query to only return information related to them
index="folks" User="Abdullah-work\\HelpDesk" process_name IN (fun.exe, Microsoft-Update.exe, Better-to-trust.exe)| table _time Description EventID process_id cmdline ParentProcessId ParentCommandline | dedup process_name
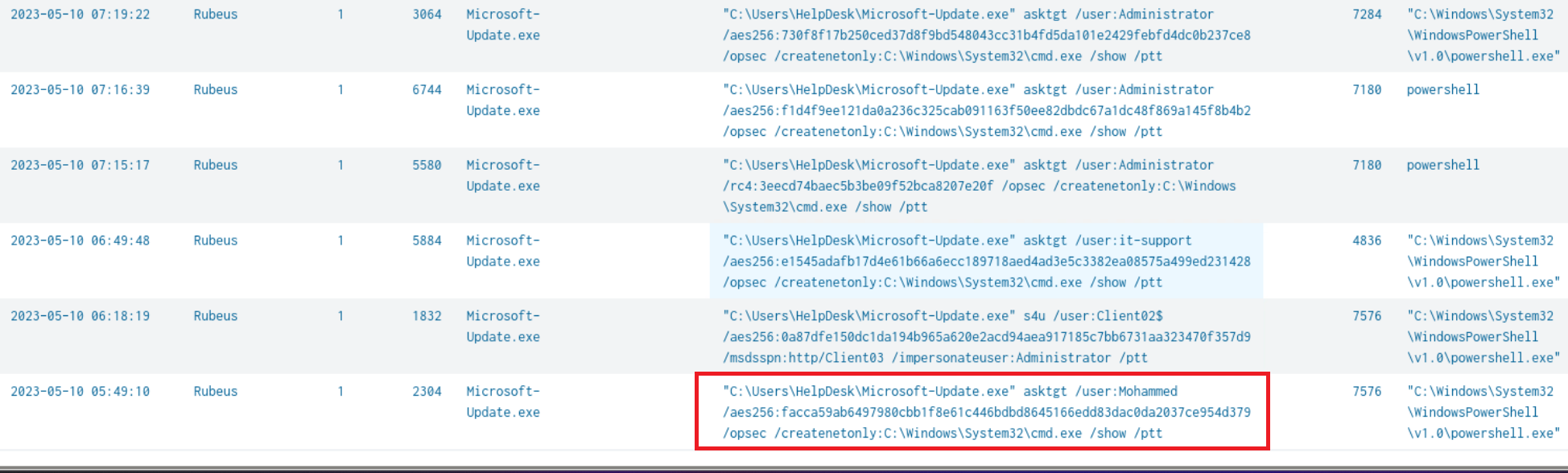
I noticed that the attacker seemed to have ran the command on several users the answer is Mohammed’s aes256 hash, (I tried the rest…they did not work haha).
Q10) Machine:Target1 What service did the attacker abuse to access the Client03 machine as Administrator?
Leveraging the same search query from Q9 on the second to last entry process id 1832 we see the threat exploiting the http/Client03 service.
Q11) Machine:Target1 The Client03 machine spawned a new process when the attacker logged on remotely. What is the process name?
index="folks" host-CLIENT03 EventID=1 cmdline!="*splunk*" | table _time User process_name process_id cmdline parent_process_name parent_process_id ParentCommandLine" used the since date time filter and set it after 5/10/23 06:18:19.000 (time the command was issued on the Client02 machine)
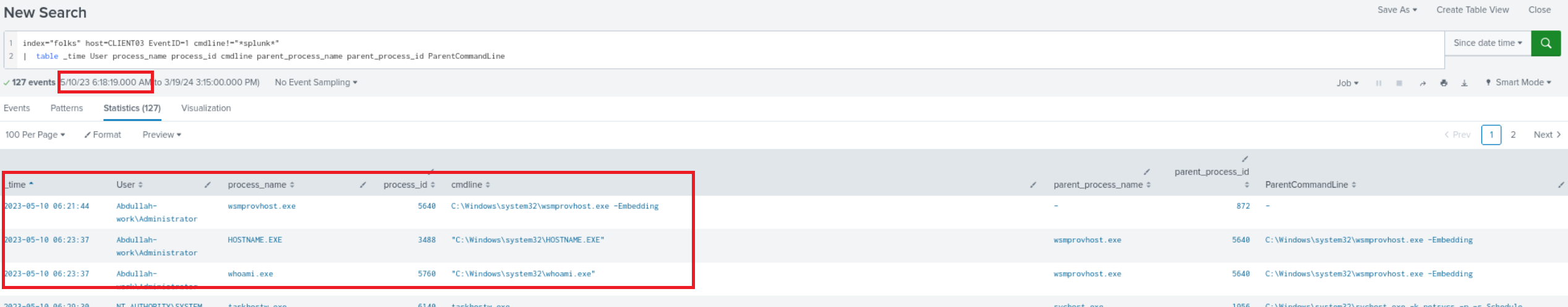
We see the process that was created after the attacker logged in was “wsmprovhost.exe” which is linked to remote sessions, we also see the use of “hostname” and “whoami” commands ,typical behavior for an attacker verifying their login was successful.
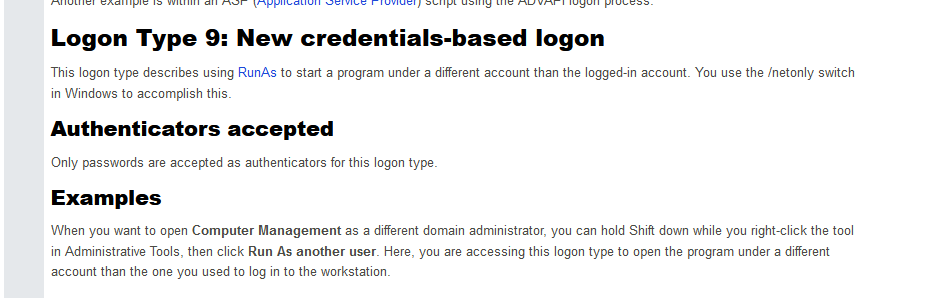
Q12) Machine:Target1 The attacker compromises the it-support account. What was the logon type?
I encountered some difficulty while attempting to find the answer to this question. At first, I was trying to correlate the logonid with some other fields such as the time but that unfortunately did not yield any results, so I went back to the command that was used copied it, and submitted it to chatgpt to see if any clues can lead me to the logontype used.

Did a quick Google search for confirmation.
In the command we clearly see the use of “createnetonly” which will used the creds specified to open cmd.exe.
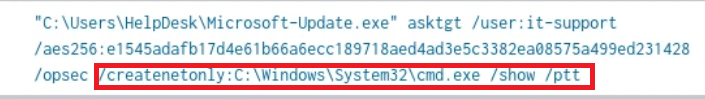
LogonType:9
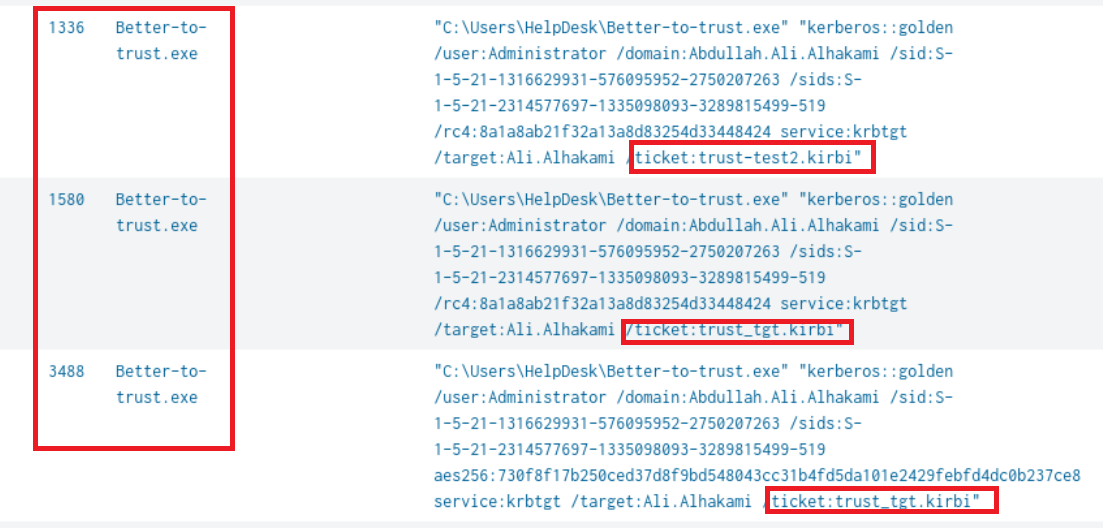
Q13) Machine:Target1 What ticket name did the attacker generate to access the parent DC as Administrator?
Found employing the same query from Q9, Better-to-trust.exe processes 1580,1336, and 3488 cmdline flags all include the ticket name.