AWSRaid CyberDefenders-Writeup
Scenario:
Your organization uses AWS for hosting critical data and applications. An incident has been reported involving unauthorized data access and potential exfiltration. The organization’s security team has detected unusual activities and needs to investigate the incident to understand the scope, identify the attacker, and prevent further data breaches.
Q1) Knowing which user account was compromised is essential for understanding the attacker’s initial entry point into the environment. What is the username of the compromised user?
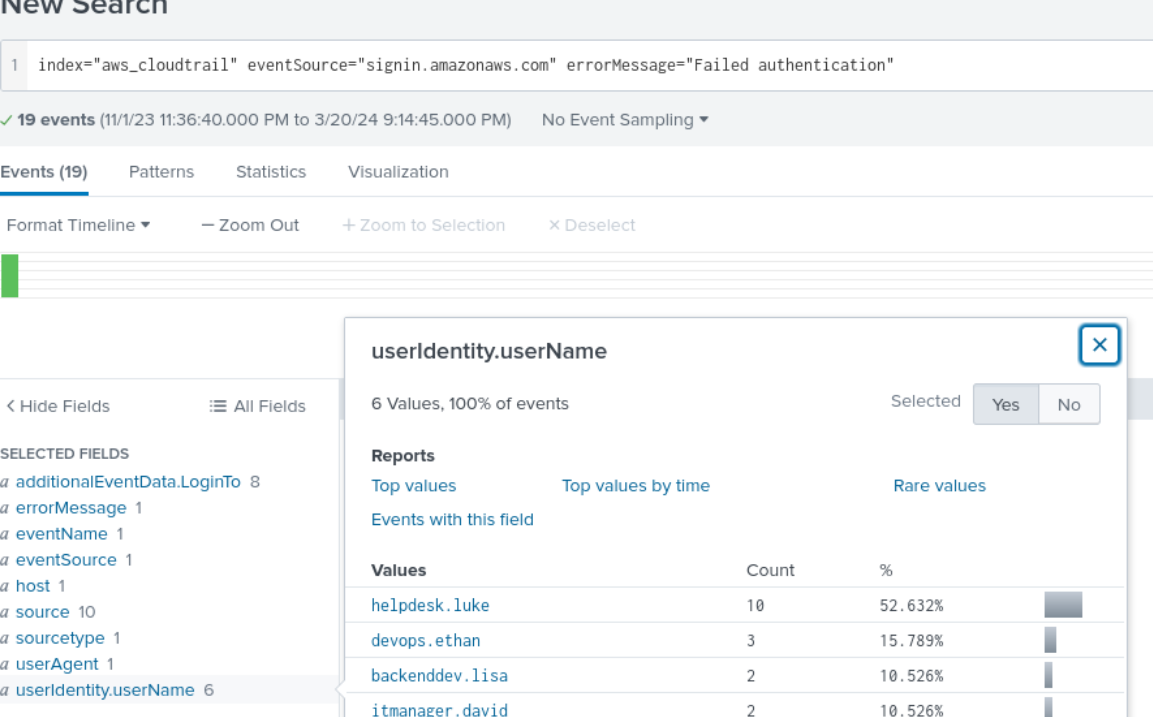
Using the signin event source and the failed authentication error message filter I was able to deduce there was some brute-forcing going on given the numerous failed authentication attempts on the helpdesk.luke account from the 185.192.70.84 IP address. This happened in less than a minute 11/2/23 9:53:27:000 AM - 11/2/23 9:54:00:000 AM. The user agent was Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36. They successfully logged in at 11/2/23 9:54:04.000 AM.
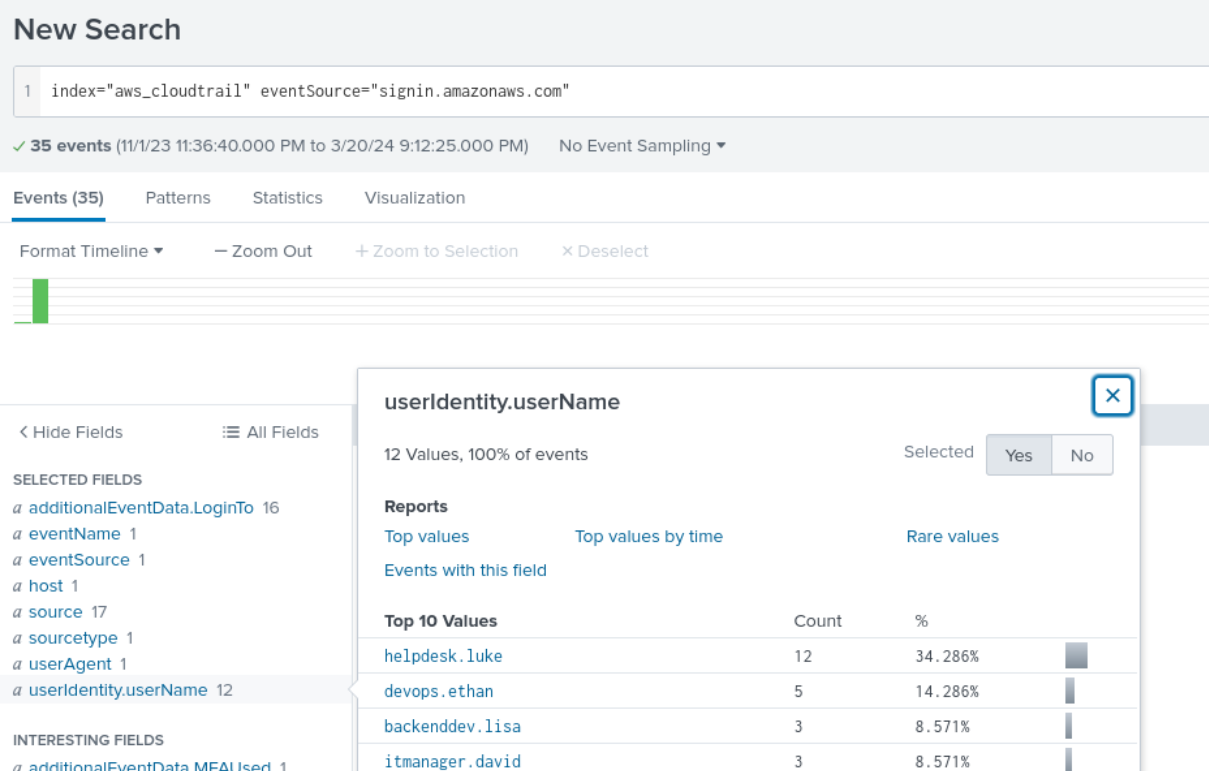
Q2) We must investigate the events following the initial compromise to understand the attacker’s motives. What’s the UTC timestamp of the attacker’s first access to an S3 object?
Given the question specified s3, I filtered for that particular event source along with the compromised account and a few extra fields that could potentially provide more context.
index="aws_cloudtrail" "userIdentity.userName"="helpdesk.luke" eventSource="s3.amazonaws.com" | table _time eventName eventCategory requestParameters.bucketName request.Parameters.Host errorMessage errorCode
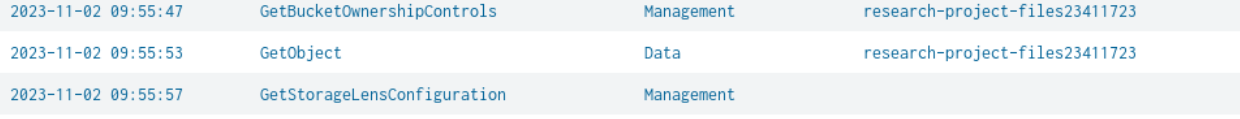
The question supplies us with a vital detail, “first access to an s3 object” object being the keyword here I submitted two wrong answers before I took a pause and realized I was looking at the first interaction with the buckets, not the objects inside the buckets. The event name you are looking for is “Get Object”.
Retrospectively, I’d refine the query to include eventName="Get Object".
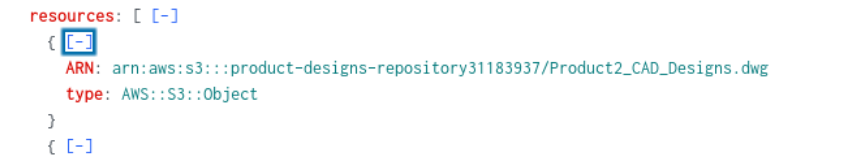
Q3) Among the S3 buckets accessed by the attacker, one contains a DWG file. What is the name of this bucket?
Utilizing the query for Q2 I just added dwg before the pipe and got one event, expanded it, and found the answer.
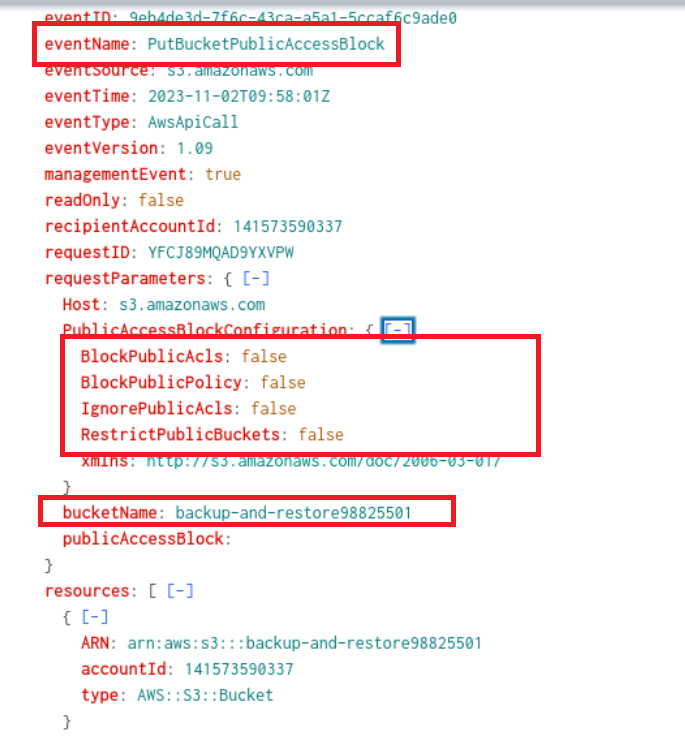
Q4) We’ve identified changes to a bucket’s configuration that allowed public access, a significant security concern. What is the name of this particular S3 bucket?
The adversary interacts with a variety of buckets but he only changes the public access configuration settings on one, which can be detected by including the event name “PutBucketPublicAccessBlock”.
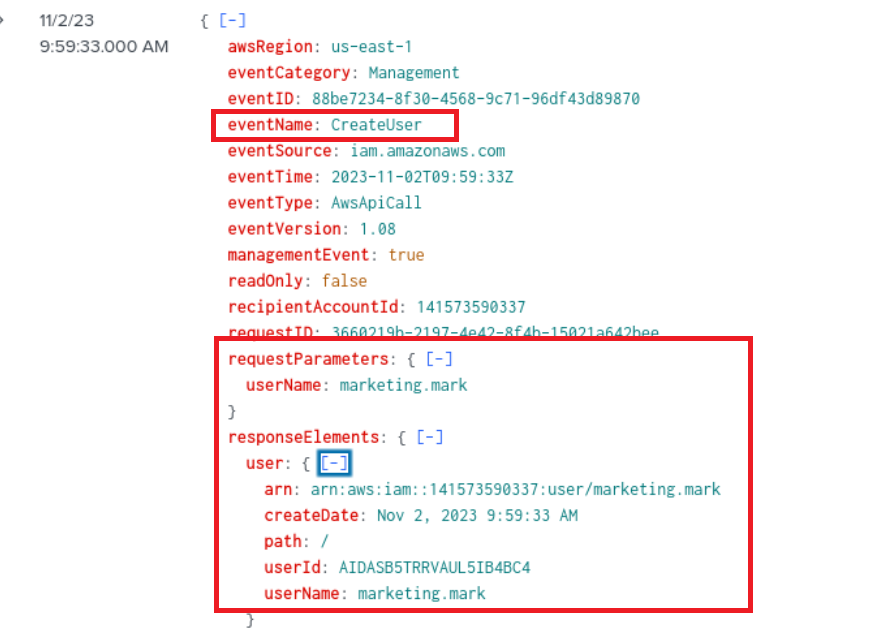
Q5) Creating a new user account is a common tactic attackers use to establish persistence in a compromised environment. What is the username of the account created by the attacker?
I hypothesized that the event to create a new user would be categorized in the “Management” category. To verify this, I targeted the management category and the frequency of the events within it.
index="aws_cloudtrail" "userIdentity.userName"="helpdesk.luke" eventCategory="Management" | stats count by eventName
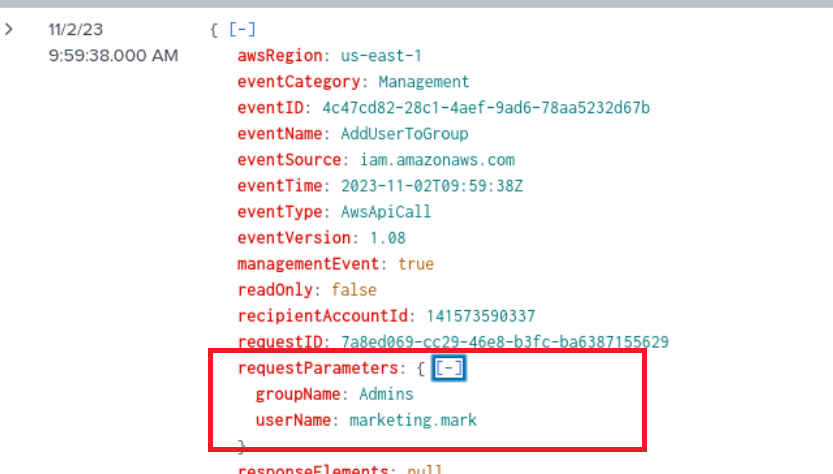
The query revealed several events, notably the “CreateLoginProfile” “CreateUser” and “AddUserToGroup” events. I subsequently expanded each entry to ensure they were all related to the attempt at maintaining persistence, which was confirmed.
Q6) Following account creation, the attacker added the account to a specific group. What is the name of the group to which the account was added?
Found in Q5, or you can simply filter for the eventName “AddUserToGroup”.